Data is the most valuable commodity today; which means that cyber crime is the most ‘lucrative and profitable industry’ for modern criminals and the biggest threat for modern businesses. Cyber attacks can no longer be prevented by simply installing firewalls or antivirus software. Hackers are continuously honing their skills and devising new ways to penetrate into the system.
The number of companies experiencing security breaches is on the rise – The number of data breaches in the U.S. increased from a mere 662 in 2010 to over a thousand by 2020. One of the important tools that businesses have at their disposal to achieve security is data encryption.
Hacks continue to proliferate in both small and large organizations which indicates the lack of sufficient cybersecurity protections.
This article discusses the importance of data encryption for businesses to protect their own as well as customers’ sensitive data, types of data encryption, data encryption algorithms and the future of encryption, among other crucial topics. By the end of this article, we hope to have painted a clear picture to depict the vitality of data encryption in our bid to fight cyber criminals and thwart data theft attempts.
What is Data Encryption?
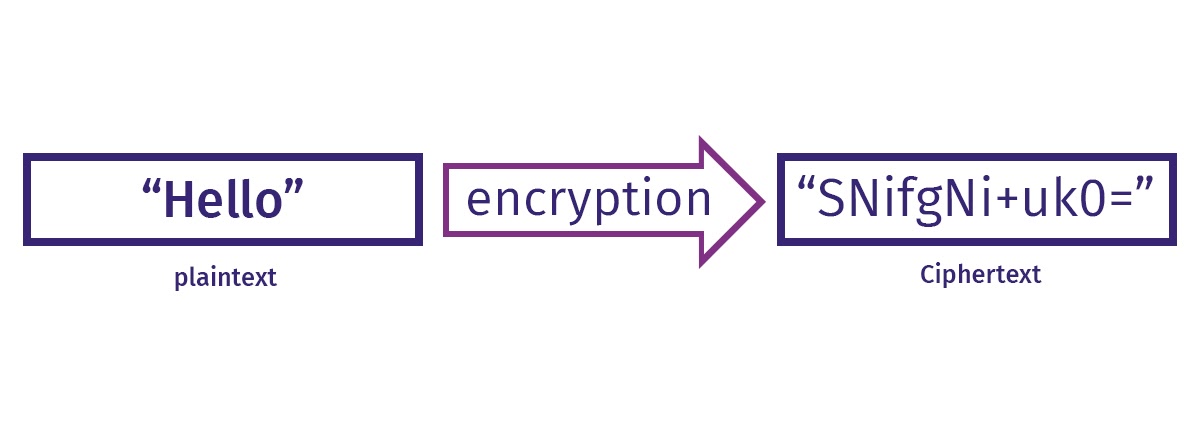
Data encryption is the process of encoding data so that it becomes unreadable for anyone who attempts unauthorized access. Encryption when implemented in conjunction with other security measures can greatly reduce the risk of security threats. Data encryption ensures that only a person with the correct encryption key can read the data.
Encryption is all about securing the communication between client apps and servers. Data is translated into another form or code so that people with access to a key or password can access the data. Encrypted data is also referred to as cipher text.
How Data Encryption Works?
Implementing data encryption is critical to secure both data in transit and data at rest. The first step in encryption is to scramble numbers, letters or symbols into some other characters. This means human readable text is converted into incomprehensible text with an encryption algorithm and key.
Encryption makes use of a cryptographic key which is a set of mathematical values. Neither a computer or human can read the data without the key. Only the right key grants permission to the reader to turn the data back to plain text. A complex cryptographic key translates to a more secure encryption.
Benefits of Data Encryption
It is important to protect data in all states and data encryption serves as an effective measure against potential thefts. Businesses that transfer large amounts of data must have encryption in place to avoid serious security breaches that can cost them hard earned money and reputation. The below mentioned benefits of data encryption will help you understand why it is a common practice for businesses to implement a suite of encryption technologies.
Complete Data Protection
Encryption protects data in all states. Business owners don’t have to worry about data getting exposed or stolen no matter how sensitive the nature of information is. While firewalls can protect your data from unauthorized access to some extent, there is nothing you can do if hackers successfully get past the perimeter security solutions. If you have encrypted your data, it would be too difficult for hackers to decode. The hacker can’t make sense of the data due to encryption. The chances for a hacker to succeed at brute force attacks is also less.
Security Across Multiple Devices
Since data passes through multiple devices, businesses need to ensure that data security is not compromised in any manner. This has especially become relevant in today’s remote work environment. Companies have little control over how employees are sharing and accessing data. While there may be security threats lurking in different devices, encryption guarantees that the data cannot be decoded. It ensures that data is safe and secure across any device.
Guarantees Data Integrity
Manipulating or altering data is another security concern encountered by businesses. Data manipulation attacks can happen on-premises or in the cloud. Encryption offers protection against data alteration and helps the recipient understand in case the data has been tampered with.
Ensures Compliance
Several industries have explicit regulations that emphasize data privacy. The healthcare industry has HIPAA that governs the storage of sensitive patient data. FIPS, FISMA, FCPA, FERPA and PCI DSS are some of the data protection regulations which businesses need to adhere to depending on the industry they operate in. Organizations that fail to comply with these regulations will attract hefty penalties.
Protects Intellectual Property
Intellectual property theft is a serious concern these days. Intellectual property such as patents, copyrights, trademarks, trade secrets need to be guarded against theft or manipulation. Data encryption helps tackle unauthorized use or reproduction of copyrighted material.
Enhance Consumer Trust
Data breaches have raised concerns among customers about the safety and privacy of their data. As a responsible business that values its customers, you should follow security best practices. By assuring customers that your business conforms to certain encryption standards to prioritize data privacy, you easily gain an advantage over your competitors. Investing in encryption technology can help gain customers’ trust.
Types of Data Encryption
Encryption methods fall into two main categories depending on how the sender and receiver share the keys and handle the encryption and decryption process. The two most common methods are asymmetric and symmetric encryption.
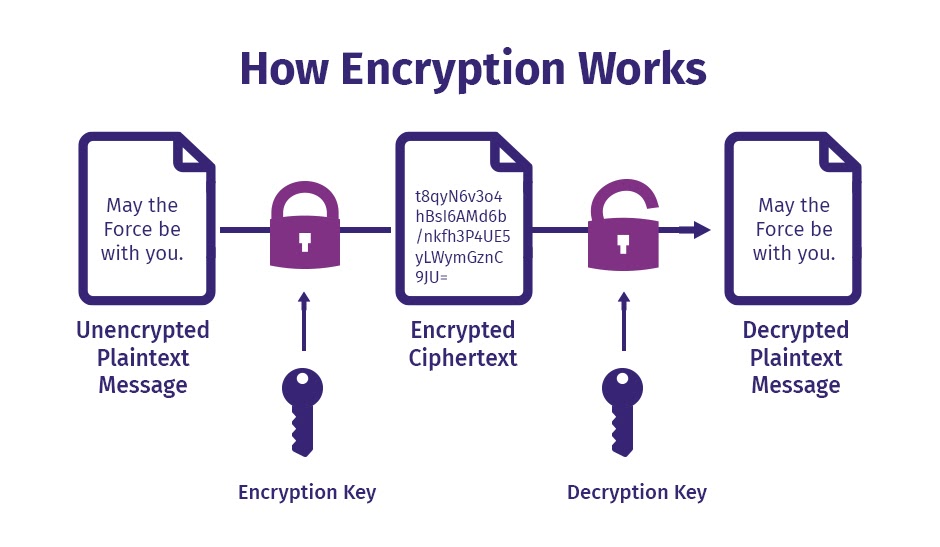
Symmetric Encryption
This type of encryption utilizes just one secret key for both encoding and decoding information. Both the sender and receiver use the same key making it most suitable for applications in closed systems. There are chances of interception by a third party in this type of encryption if the key is being transmitted to the receiver for decryption.
Source: The SSL Store
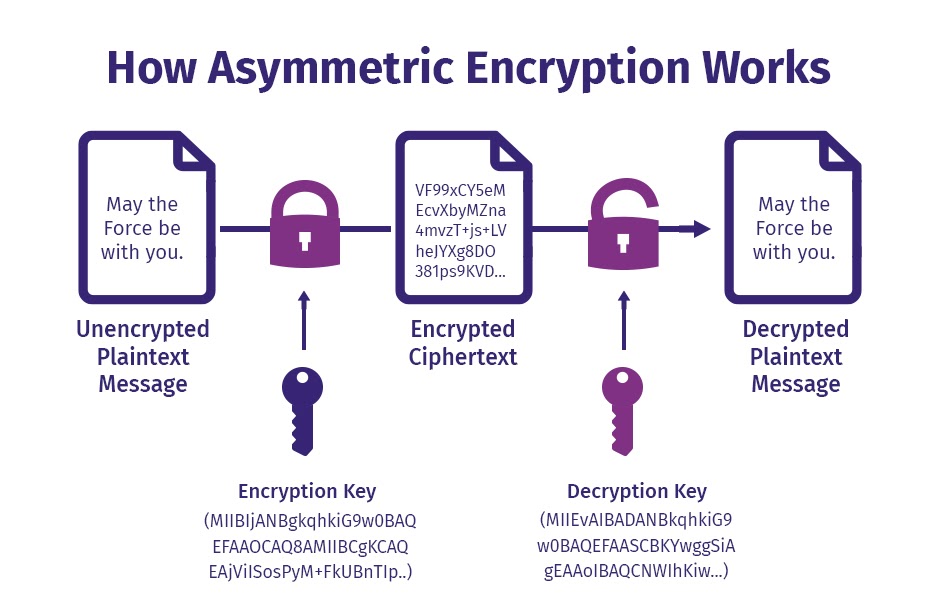
Asymmetric Encryption
Also known as public key encryption, there are two keys involved in this type of encryption. One key for encryption and the other for decryption. These keys are not identical but are mathematically linked. The public key is used for encryption which can be shared with anyone. The private key used for decryption is shared only with authorized users.
Source: The SSL Store
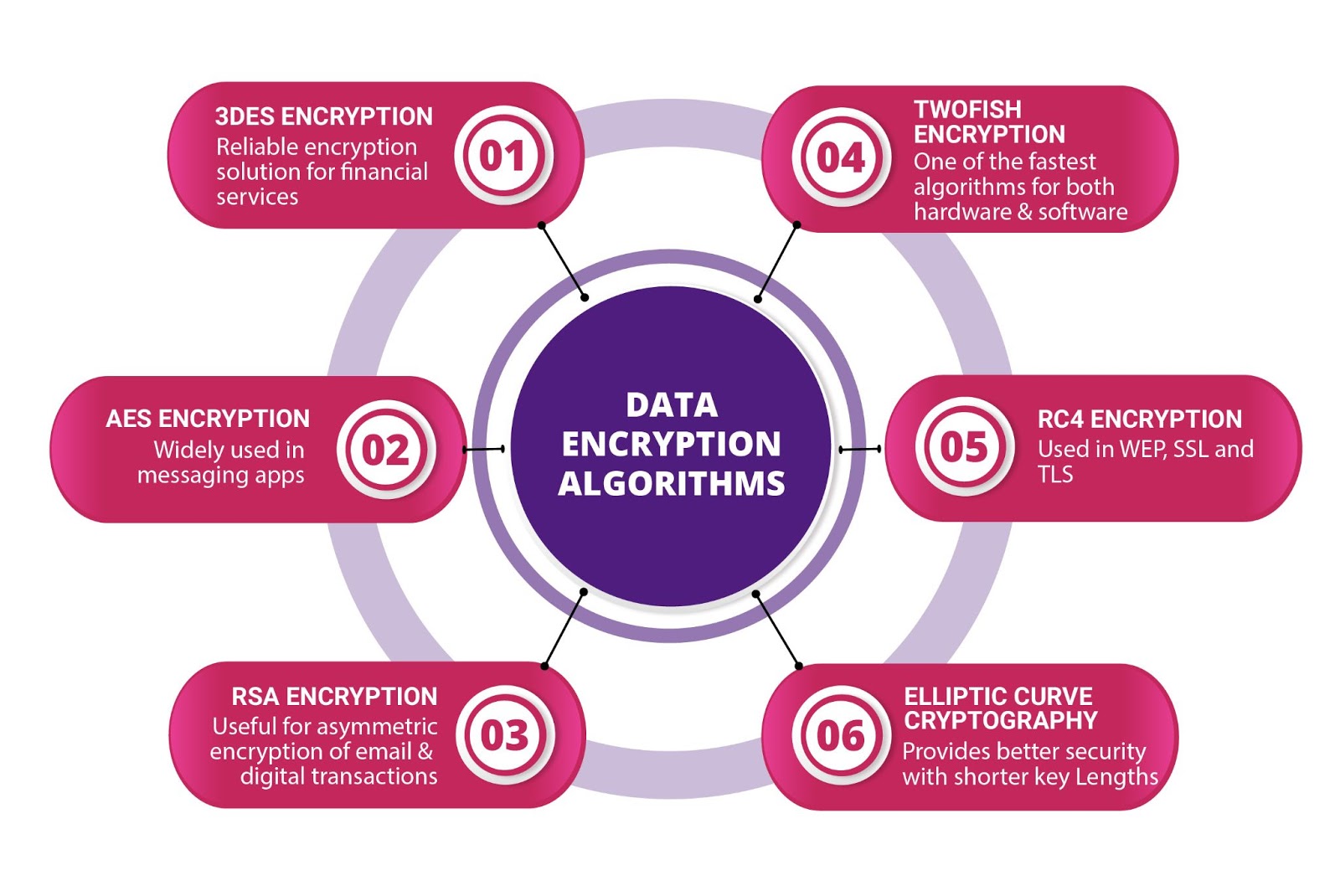
Data Encryption Algorithms
Data encryption algorithms are basically rules and instructions governing the encryption process. The effectiveness of the encryption depends on the key length, features and functionality of the encryption system.
Encryption algorithms have evolved over the years to counter sophisticated attacks launched by malicious actors. There are numerous encryption algorithms that meet different security needs out of which the commonly used ones are mentioned below.
3DES or TDES Encryption
Known as Triple Data Encryption standard, this is an advanced version of DES block cipher. This algorithm creates a longer key length by encrypting, decrypting and encrypting again. While DES had a 56-bit key, 3DES runs the 56-bit key thrice to make it a 168-bit key.
The encryption works in three phases – encrypt, decrypt and encrypt. The decryption phase likewise would be decrypt, encrypt and decrypt. While 3DES is slowly losing its popularity today, it is still used for hardware encryption purposes in financial services.
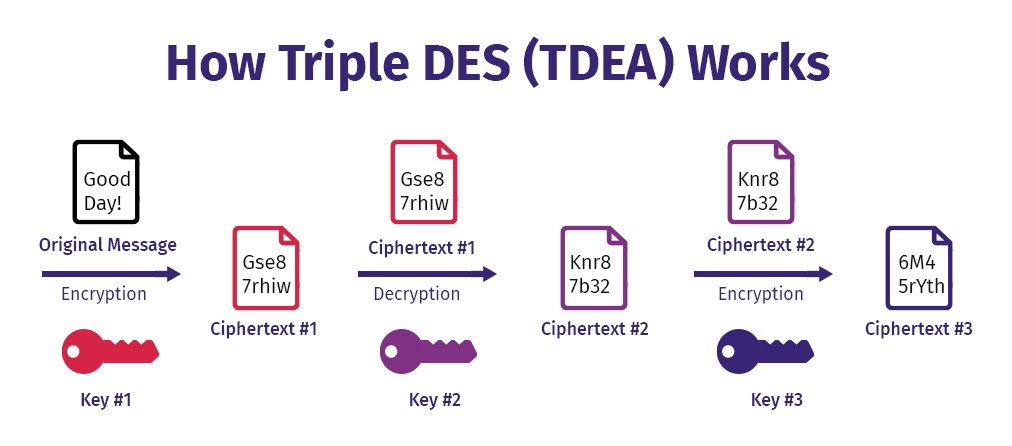
Source: Security Boulevard
AES Encryption
AES stands for Advanced Encryption Standard which is a symmetric key encryption based on Rijndael algorithm. Established as the US government standard for encryption, it is available in 128, 192, and 256 bit sizes. The number of rounds of encryption increases with an increase in key length. For instance, 128-bit will have 10 rounds whereas 192-bit will have 12 rounds. It has applications in both hardware and software and is widely used to encrypt messaging apps.
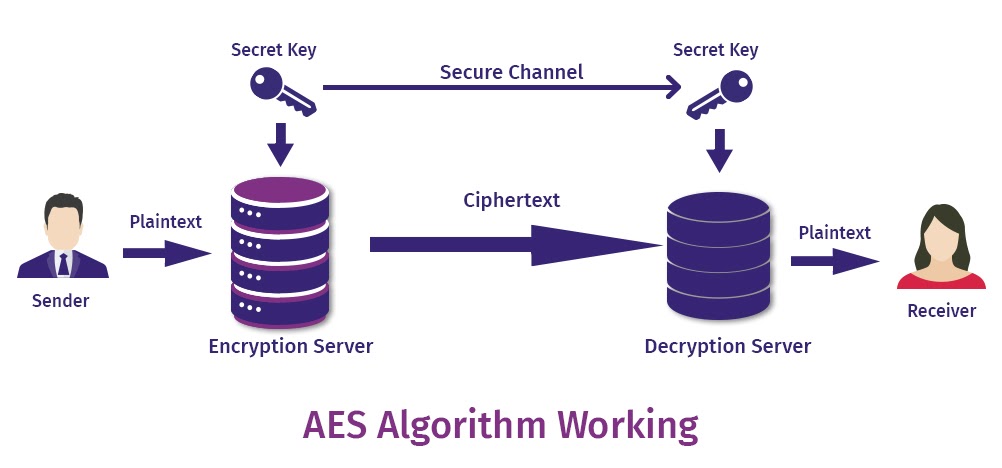
Source: Trenton Systems
RSA Encryption
This encryption is popular for its long-key length. It is named after Rivest, Shamir, and Adleman – the surnames of the mathematician who first described the algorithm. It is one of the widely used asymmetric cryptography for securing data in transit as it involves a pair of keys. RSA encryption can be broken only with large amounts of computing power. Security protocols like SSH, S/MIME, OpenPGP, and SSL/TLS and browsers use RSA encryption.
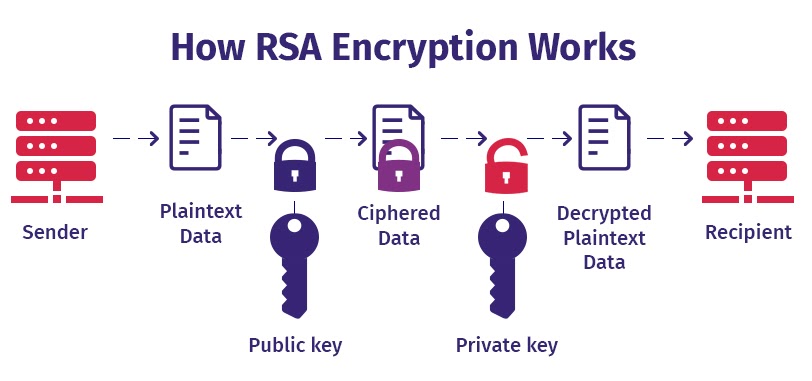
Source: Sectigostore
Elliptic Curve Cryptography
Elliptic Curve Cryptography (ECC) is an improved version of RSA that guarantees security with shorter key lengths. ECC enables faster generation of keys and signatures. Compared to RSA, ECC uses less memory. ECC is thus beneficial for use in mobile devices.
Twofish Encryption
This is one of the fastest algorithms with a complex key structure. A symmetric block cipher, this encryption functions in 16 rounds. This encryption is license free and is available in 128, 196, and 256 bit sizes. Twofish encryption is ideal for use in hardware and software environments.
Source: Schneier
RC4 Encryption
RC4 encryption is a stream cipher that is easy to implement. RC4 encryption functions well with large streams of data easily and swiftly. RC4 is used in protocols like WAP, SSL and WPA. Also used in IEEE 802.11 wireless LAN std, simplicity and speed of operation are its key features.
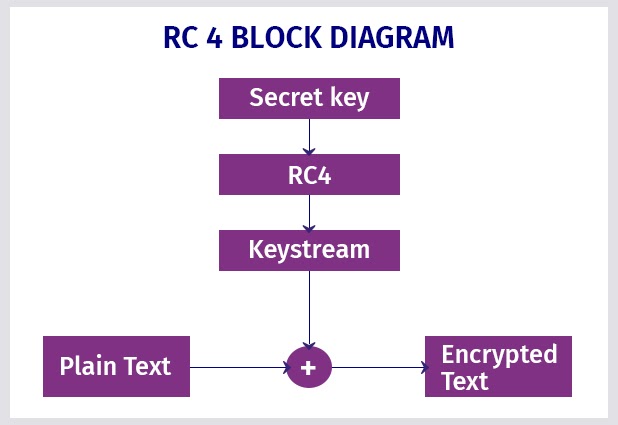
Source:GeeksForGeeks
Data Encryption Standard (DES) and Blowfish are among few other best known encryption algorithms. DES is now obsolete and no longer suitable for modern day security needs. Blowfish is one of the flexible encryption methods and is known for its tremendous speed. It is freely available in the public domain.
End to End Encryption
End to end encryption (E2EE) secures both ends of the conversation. It is one of the safest ways for secure online communication. E2EE differs from regular encryption in that even the service provider cannot read the content of your message. E2EE is considered to be more effective than standard encryption since no hacker, government agencies or even the service provider that facilitates your communication possess the decryption key. WhatsApp is an apt example of messaging applications that have implemented E2EE.
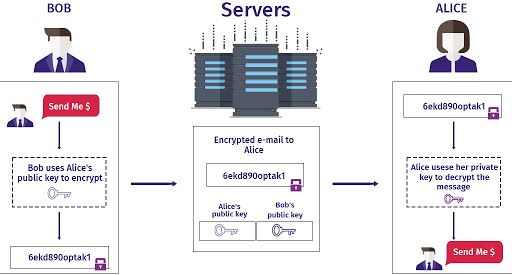
Source: Preveil
Common Criteria
Common criteria for Information Technology Security Evaluation, commonly referred to as CC, is not an encryption standard. Rather it is a set of international guidelines that verifies whether IT products fulfill certain security requirements. The purpose of CC guidelines is to provide vendor-neutral and third-party oversight of security products. Vendors voluntarily can submit the products for review and whole or individual functionalities would be examined. Depending on the product type, the features are tested in accordance with a defined set of standards. While encryption was initially beyond the scope of CC, it is now being included within CC security standards.
Future of Data Encryption
Data encryption is evolving to help organizations successfully counter current and emerging security threats. Though brute force attacks are difficult to execute, hackers have been successful in stealing data through various advanced techniques. Confidential computing, quantum-safe cryptography and fully homomorphic encryption are the three critical emerging technologies in data encryption.
In the future, encryption algorithms are expected to include biometric authentication and voice recognition. There is also something known as ‘Honey Encryption’ to make it challenging for hackers to steal data. With honey encryption enabled, a hacker carrying out a brute force attack won’t be able to figure out if he successfully guessed the key.
Usually hackers know if their attempts have been unsuccessful as the decrypted results would be unintelligible. But Honey Encryption tricks the hacker into believing that he rightly guessed the password by generating phony results that appear to be genuine. The emerging encryption technologies will help organizations to better address nefarious activities.
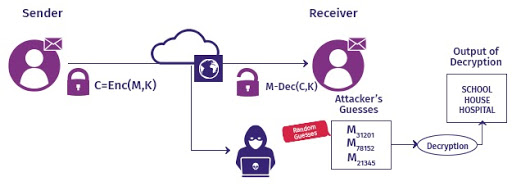
Source: Researchgate
Final Thoughts
Encryption must be an integral part of the security mix of organizations to safeguard business-sensitive data. Advanced data encryption is critical to facilitate the secure growth of digital ecosystems.
Here is a quick recap of the important points discussed in this article:
- Implementing appropriate data encryption protocols is an important line of defense in the cybersecurity architecture
- Data encryption is an effective way to protect data confidentiality in this worsening cyber threat environment.
- Encryption works by encoding plain text into cipher text. The sender encrypts the data before transmitting it via digital channels. The authorized recipient decodes the data with the right decryption key.
- Encryption ensures complete protection of data both at rest and in transit.
- Hackers won’t be able to decipher encrypted data even if they somehow gain access to it.
- There are two methods of encryption namely asymmetric and symmetric. Symmetric encryption is quick and easy to implement as it uses a single private password for both encoding and decoding. Asymmetric encryption, on the other hand, uses a public key to encrypt and a private key to decrypt.
- The benefits of data encryption include secure transmission, compliance with regulations, security across multiple devices, customer trust, competitive edge, data integrity and protection against intellectual property theft.
- The most commonly used encryption algorithms are 3DES, AES, RSA, ECC, Twofish, RC4, Blowfish among others.
- End to end encryption (E2EE) protects data from being deciphered by anyone except their intended recipients.
- The future of data encryption will witness more advanced methods of encryption like Honey Encryption, Confidential computing, Quantum-safe cryptography, Fully homomorphic encryption and also encryption algorithms with biometrics and voice recognition.
AppSealing is a leader in providing cloud-based in-app security solutions for protection from unauthorized access. With affordable solutions that guarantee robust security, it not just protects data but offers valuable insights and threat analytics on attack vectors. Protecting more than 800 applications worldwide, it’s security solutions can be implemented with zero coding and no negative impacts on app performance. Contact our team today for end-to-end protection of Android, iOS and hybrid applications.