Cyberattacks are now a forceful reality, having a ubiquitous presence due to the evolution of multiple devices, which humans use to communicate with one another, and humongous personal and corporate data at stake. Together, these attacks have resulted in ballooning the cost of tackling cybercrime and their associated repercussions.
Understanding the types of cyber attacks and the different techniques employed by attackers to execute them can go a long way in establishing appropriate security frameworks. This proactive approach to internalizing application security is essential to protect businesses from the threats of cyberattacks and maintain business revenue with unwavering customer loyalty. But before that, it seems pertinent to ask a basic question:
What is a Cyber Attack?
According to Cisco, a cyberattack is “a malicious and deliberate attempt by an individual or organization to breach the information system of another individual or organization. Cybercriminals carry out these attacks using one or more computers by exploiting the existent loopholes and employing one or multiple attack vectors to destroy, alter, disable, or gain unauthorized access to the nodes or assets in the network.
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.

Cyberattacks are now a forceful reality, having a ubiquitous presence due to the evolution of multiple devices, which humans use to communicate with one another, and humongous personal and corporate data at stake. Together, these attacks have resulted in ballooning the cost of tackling cybercrime and their associated repercussions.
Understanding the types of cyber attacks and the different techniques employed by attackers to execute them can go a long way in establishing appropriate security frameworks. This proactive approach to internalizing application security is essential to protect businesses from the threats of cyberattacks and maintain business revenue with unwavering customer loyalty. But before that, it seems pertinent to ask a basic question:
What is a Cyber Attack?
According to Cisco, a cyberattack is “a malicious and deliberate attempt by an individual or organization to breach the information system of another individual or organization. Cybercriminals carry out these attacks using one or more computers by exploiting the existent loopholes and employing one or multiple attack vectors to destroy, alter, disable, or gain unauthorized access to the nodes or assets in the network.
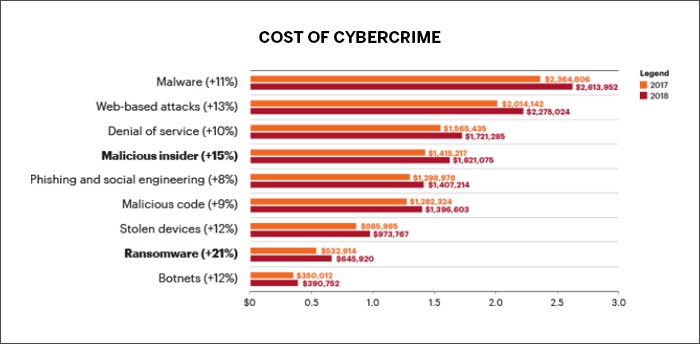
Source: Accenture
According to Accenture’s 2019 “Cost of Cybercrime” study, there has been a mammoth 67 percent increase in security breaches over the last five years. The total value of risk arising from these cyber crimes is pegged at a mammoth USD 5.2 trillion over the next five years.
The motives of criminals can be as simple as obtaining your financial details as lethal as breaching databases containing critical personal identifiable information (PII) of customers, attacking infrastructure to distribute malware, etc. It will be pertinent to have a look at the major categories of cyberattacks, and why a one-size-fits-all approach does not help in countering them.
Classification of Cyber Attackers
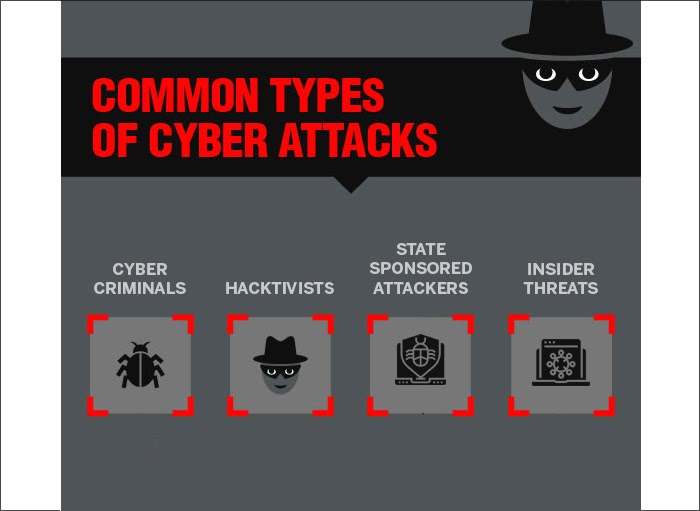
Though the purpose of a cyberattack is always malicious, the hacker may use several tools and techniques to perpetrate the attack. Depending on their intent and the end objective, cyber attackers can be roughly grouped into:
Cyber-criminals
They are individuals or groups of individuals who target company information, customer data, or other critical data and try to monetize it on the dark web. They make use of sophisticated tools and techniques, use computer/mobile devices as a medium to perpetrate intelligent, hard-to-discover malicious cyberattacks.
Hacktivists
They have a non-financial agenda to propagate. They may perform an attack to reinforce their belief system, which could be political agenda, religious ideology, or a cause which they want to be made known through their digital malfeasance. Depending on the political beliefs they hold, they can be described as progressive, ethical, or plain disruptions among other categories.
State-sponsored attackers
They carry out cyberattacks targeted at a particular country to destabilize its social, economic, or military administration through the support of the country of their origin. They could perpetrate lone wolf attacks as well, showing allegiance to a particular state.
Insider threats
They originate from employees, contractors, third-party affiliates of an organization and are hard to detect and prevent because of the trust factor involved. These attacks could be either malicious, accidental, or carried out due to pure negligence.
Further, cyberattacks fall into two groups based on the attack’s end-point:
- Web-based cyber attacks, if the hacker targets a website/web application; or
- The system-based cyberattack, if the attack’s purpose is meant for compromising node(s)/system(s) in a network.
Types of Cyber Attacks
Phishing
What is a Phishing Attack?
Phishing is prevalent everywhere and growing rapidly by the day. It is an attempt to steal critical PII like user credentials, financial details like credit card details, and anything that has potential value by masquerading oneself as a trustworthy entity. This lures the target in divulging the details without any doubts whatsoever.
Types of Phishing attacks
At its core, phishing exploits human impulses through an attractive message or offer. Attackers usually resort to phishing attacks by targeting large groups and hence increase the chances of at least some targets falling victim to the attack. A typical example of a phishing attack involves the attacker impersonating an individual or establishment and sends emails to unsuspecting targets asking for immediate help with a link attached to the communication. The innocent user clicks on the link, which takes them to a fake website that looks similar to a legitimate website. The person, unaware of the trap, falls into it and ends up sharing personal details with the attacker, who then robs the user even before they realize that they have been attacked.
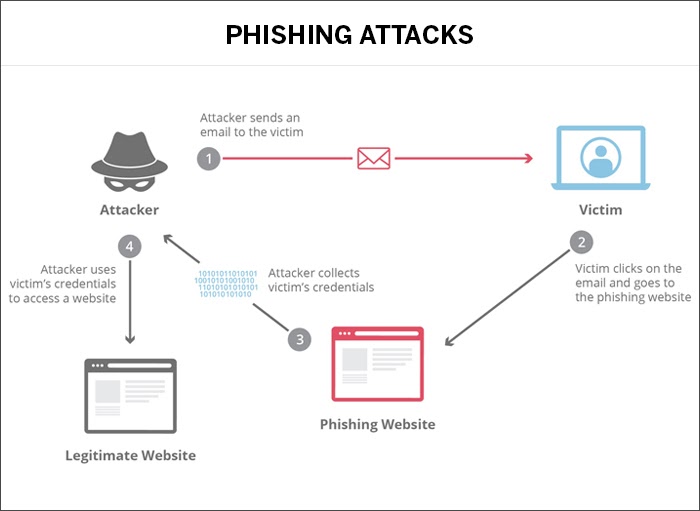
Source: Cloudflare
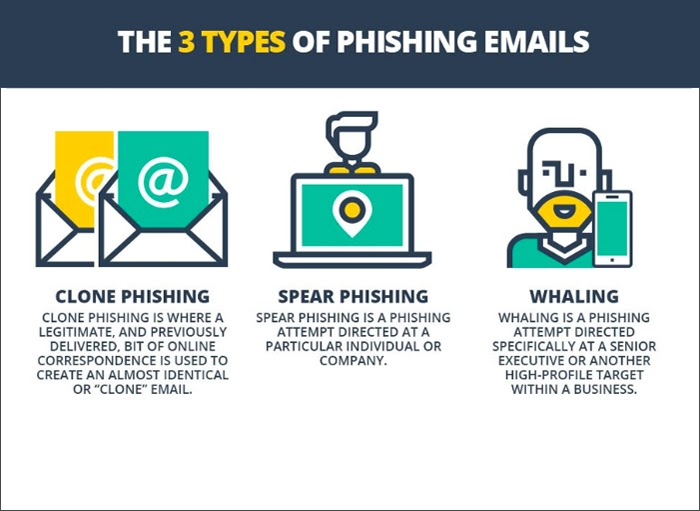
To make the attack more personalized and authentic, attackers use the spear-phishing method, which involves including detailed information, like a proposal with banner, logo, some prominent names, website addresses, etc., which lends more credibility to the communication and helps lure more targets to share sensitive information. If an organization’s management is the main target of a phishing attempt, it is known as whaling. A successful whaling attack could result in windfall gains for the attacker.
Clone phishing benefits from the legitimate communication already exchanged with the target. The hacker clones the legitimate message but inserts specific changes to trap the target by using malicious attachments, invalid links, etc. This attack takes advantage of the trust reposed by the target on previous legitimate communications and forces the innocent target to perform actions as desired by the malicious attacker.
Source: Coolwallet
As seen above, phishing involves spoofing of one way or another – attackers develop pseudo-websites to pose as authentic websites or create URL homographs to trigger user clicks on website URLs which look-alike but are actually malicious. In some cases, attackers use HTML or JavaScript to spoof website addresses so that an innocent user sees authentic website URL only, redirecting the user from an authentic website to the attacker-controlled website based on actions. To accomplish these goals, the attacker first compromises the authentic website and then carries out a seamless attack, so that the user does not know about it.
Example of Phishing Attack
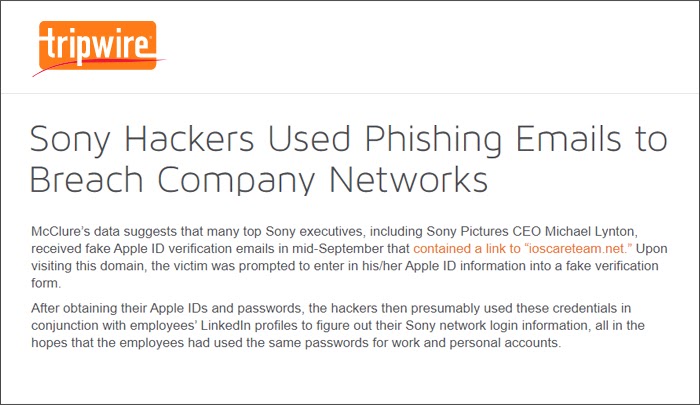
In 2014, the network of Sony Picture Entertainment became a target of a phishing attack. Hackers sent fake emails to many employees of the company, including its CEO Michael Lynton, asking them to verify their Apple IDs. The verification links in the emails took employees to ioscareteam.net and collected their user credentials. Hackers tallied these credentials to employees’ social media credentials and obtained login details of Sony’s network. Hackers are said to have inserted a malware Wiper into Sony’s network through this route and stolen many documents in the process.
Guarding Against Phishing Attacks
To combat phishing attacks, it pays well to verify email senders and download attachments only when it is essential. Organization users and third-party vendors should be continuously educated using case studies about the importance of security and how they could prevent themselves from falling into the phishing trap. Emails asking for financial help should trigger alarm bells in the user’s mind. Enterprises should forbid their employees from opening emails that come from non-trusted sources.
Implementing a good quarantine email engine that can monitor emails, attachments, and short URLs from suspicious origins and filter/quarantine them can be helpful in handling phishing attacks. Organizations can also conduct penetration testing assessments to know their vulnerable points and redress them before an actual security event happens.
Malware
Malware is an application developed to disrupt the normal functioning of any device, be they mobile phones, desktops, or servers. Usually distributed as a script or executable code, the user clicks on the malware source and inadvertently installs the malware. This malicious application then acquires a foothold on the device and starts tracking everything depending upon its capability – capturing keystrokes, installing harmful software, stealing valuable information from the system, encrypting it to demand a ransom (ransomware), and so on.
Types of Malware Attacks
Malware comes in various forms depending on their end objective. Some malware intends to gain access to troves of information, like credentials, credit card information, etc., while others are purely disruption oriented. They are orchestrated attacks to initiate problems in a computer, rendering the system inoperable. In some cases, cyber-criminals use sophisticated malware to infect all the systems in the network to carry out a distributed denial of service (DDoS) attack.
Though malware comes in various flavors, it is useful to have a look at the most common types of malware and their ways of distribution:
Ransomware
It is a specialized malware distributed to extort money from targets and is one of the most prevalent and known cases of cyberattacks. The attacker distributes the malware as a virus to access the target computer’s hard drive. It, then, encrypts the data and makes the computer/data unusable for the user until they make the ransom payment demanded by the attacker. It is often impossible to decrypt the file’s contents by oneself. WannaCry and Maze ransomware are recent examples of how malware could wreak havoc, forcing many corporations to shell out bitcoins and money to pay for retrieving their compromised machines and data.
Virus
A virus is a self-propagating malware intended to cause maximum damage by spreading rapidly to different parts of the hard drive, including critical operating system (OS) files. It injects itself into the existing piece of software/data and spreads with an intention to infect files. This is different from Trojan horse, which is built specifically for an application and does not self-propagate.
Macro-viruses
They attach to an application’s initialization sequence and execute it when the application launches. The malware executes the instructions in the background without the knowledge of the user and attaches itself to other code in the computer covertly. This malware usually executes with Microsoft Excel and Word.
Stealth viruses
They take over OS files and system functions to conceal themselves from anti-virus software detection. They typically hide in boot sectors and partitions and are adept at avoiding detection. This means that the infected files/hard disk sectors go undetected.
Boot record virus
They infect the bootloader and attach itself to the master boot record in the hard drive. When the system boots, the infector searches the boot sector, loads into memory, and propagates into other sections of the hard disk.
Trojans
The trojan is a delivery mechanism of malware to systems by camouflaging its intentions intelligently – hence the name which is derived from Greek mythology. It usually hides in a genuine application (like games, software, etc.) and establishes a back-door for attackers to exploit and do extensive damage. Trojan horse is thus an entry mechanism for attackers to gain a foothold of the user device for further exploitation. They do not self-replicate like viruses.
Worm
The worm is a special malware designed to spread from targeted devices to other nodes in the network, unlike viruses and Trojans, which are meant for specific localized attacks. These self-contained programs are usually spread through email attachments and are activated when the user opens the attachments. It is powerful enough to distribute itself rapidly (sending emails to contacts by attaching itself as an attachment) and can spread to other computers in no time. Its ability to cause damage is multiplied by its sheer non-recognition and ability to self-propagate without any active involvement from the attacker.
Example of Malware Attack
Source: The New York Times
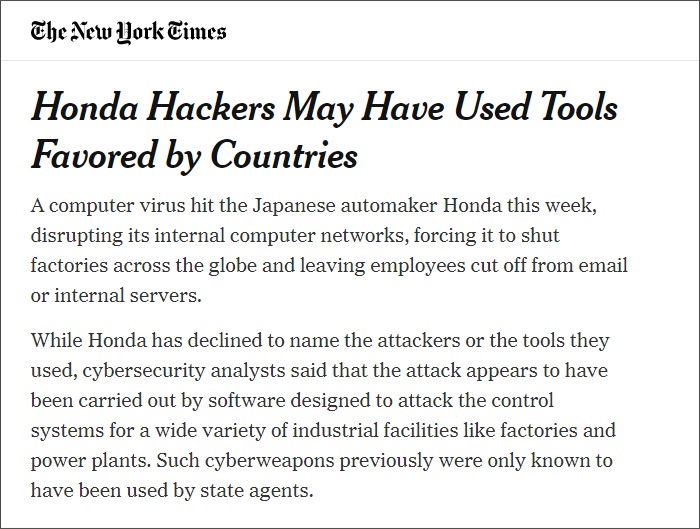
The global automotive major Honda was hit by malware in June 2020, causing its employees to be locked out of its networks, cutting off their access to emails and data. The impact of the attack was so severe that Honda had to stop production in its plants in different countries. Security analysts fear that cyberweapons used by hackers look like what rival states use to target adversaries. Hackers have earlier attacked Japanese corporations to steal their data or disrupt their communication networks, but forcing a company to shut its production line is a huge disruptive success for hackers. The company claimed that one of its US arms has been prevented to “answer calls, fund contracts, provide payoff quotes or service customer accounts.
Guarding Against Malware Attacks
The best way to protect against malware attacks is to install anti-virus software, keeping all system software up-to-date and downloading only legitimate software or applications from trustworthy stores. Following the golden rule – “think before you click” – often helps in protecting a device against malware attack.
Using a subscription-based popular antivirus software can help in detecting any suspicious activity/files with mischievous intent. Though not always foolproof, updated anti-virus software is helpful to act as the first line of defense in case of malware attacks and mitigate potential malware installation.
Planned security audits of your business-critical digital assets, like websites, mobile applications, etc., make sure that assets are free from security vulnerabilities and detect any loopholes to prevent exploitation. Imbibing this assessment as a mandatory activity guards your customers, employees, and stakeholders against malware threats and maintains their confidence in your business.
SQL Injection
Structured Query Language (SQL) is a programming language to communicate with databases. Servers often employ SQL to access and update data between the client and the database. Attackers often use malicious SQL statements to trick the systems in performing undesired and unexpected actions. Using the SQL injection (SQLi) method, the attacker can directly access and update the customer’s PII from and to databases. This cyberattack is a favorite with most attackers, as it gives them rich bounties and figures prominently in the OWASP Top 10 list of application security risks.
SQLi works by exploiting known SQL vulnerabilities and makes the server run malicious code. Passing through usual validation measures in an application, attackers exploit user interface features, like the search box, to dump critical personal information like username and password, directly from the database, thus bypassing all security measures.
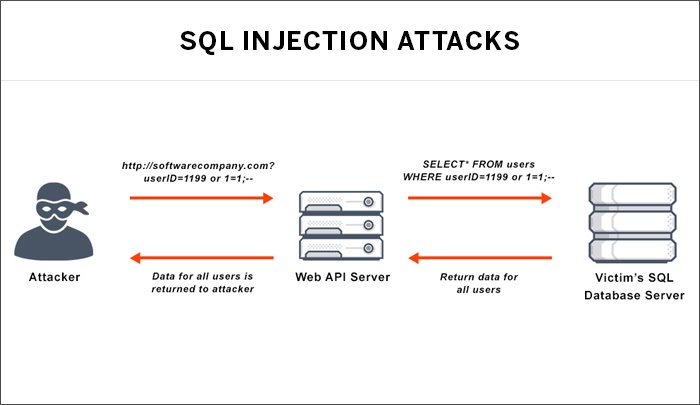
Source: Avi Networks
Some of the ramifications of a successful SQLi attack include:
- Bypassing user authentication without username/password
- Altering/adding/deleting data from databases and compromising data integrity
- Retrieving scores of customer data
- Gaining administrator/root access of an application
- Execution of OS shell and remote commands
Unlike malware and phishing, SQLi requires a deep understanding of how web applications and the client-server model of database architecture work. The attacker often keenly observes the system’s behavior for months before initiating the attack using an appropriate vector. SQLi exploits vulnerabilities arising from the usage of dynamic SQL in web applications, which is commonly seen in PHP and ASP applications (due to the prevalence of older functional interfaces).
Types of SQLi Attacks
Different variations of SQL injection attacks exist. They show the tenacity and the damage to the application in case of a successful attack. They include:
Unsanitized Input
It is an attack-type wherein the attacker keys in user input which is not properly sanitized for characters and not validated for expected text. In this case, the attacker may exploit the vulnerability by keying in character combinations which may retrieve the complete list of all customer data, which is not an expected database behavior. This data bounty could then be sold by the attacker on the dark web.
Blind SQL Injection
It does not retrieve the information from the database directly and depends on several factors which the attacker notices to perpetrate the attack. GET String query in HTTP responses, the turnaround time of retrieving information based on a search query made, asking the database a set of true/false questions, etc. help the attacker determine the database configuration. This is an advanced SQLi attack technique and used when the web page does not directly display user data. Using Blind SQLi, the attacker performs reconnaissance, obtains sensitive information, and alters database contents. They are usually perpetrated using the SQL sleep() function to command the database to sleep for a specified duration and delay the responses during that time period.
Second-Order SQL Injection
These types of attacks make use of user-submitted data stored in the database, which the attacker retrieves and makes use of in a malicious SQL statement. They use secondary system behavior (like admin triggered job) to trigger and allow the attacker to control the database.
Example of SQLi Attack
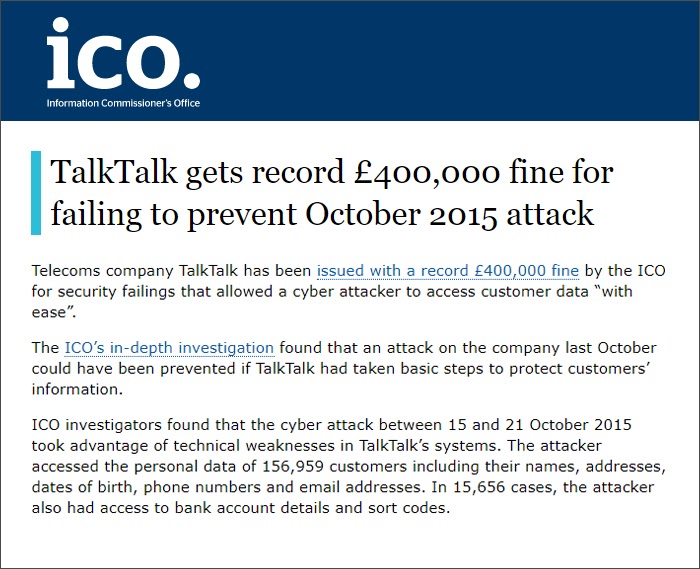
Source: ICO
In 2015, the UK’s Information Commissioner’s Office (ICO) fined the telecom company TalkTalk £400,000 for the inability to protect customer data. Hackers had managed to break into the customer database of the company, stealing data of 156,959 customers, which included personally identifiable information, like names, addresses, dates of birth, phone numbers, email addresses, and bank account details. The ICO concluded after an investigation that hackers used SQL injection techniques to compromise TalkTalk data, something the company should have guarded against since the database it was using had a known bug and its security team did not update the database to the latest release.
Guarding Against SQLi Attacks
Preventing SQLi attacks requires robust coding practices. Developers should avoid the usage of dynamic SQL in their queries as far as possible. Placing user-provided inputs directly into SQL statements allows the attacker to retrieve information directly from the database. Stored procedures and parameterized queries are usually a safer bet.
Sanitizing user inputs is also a recommended practice to prevent SQLi. The type of data should be dynamically validated to match the data type expected out of the fields. Before storing the user inputs, characters should be properly escaped.
Configuring databases the right way with bare minimum privileges will prevent the attacker from doing damage even if he/she manages to gain database access. A custom 404 page should show up in case of a database error, instead of displaying database configuration information in the web page.
At the minimum, store sensitive data like passwords in encrypted and hashed format than in clear text format. Even if the attacker manages to exfiltrate the data, they would not be able to decrypt the salted hashed password, thus circumventing the possible damage.
Updating and patching database issues at regular intervals keep the database secure and fail-proof. Not applying database patches could prove costly in the long term.
Configuring critical databases with a web application firewall helps to provide protection to public-facing apps and identifies SQLi attempts.
Denial of Service or Distributed Denial of Service Attacks
Through a denial-of-service (DoS) attack, the perpetrator seeks to make digital assets inaccessible to intended users by disrupting the services of a host connected to the internet. The attack involves flooding the host server with overwhelming requests, much more than it can handle, thus eventually triggering a crash. This makes legitimate requests from users unserviceable and exhausts resources and bandwidth. Distributed-denial-of-service (DDoS) attack happens when the source of requests come from multiple compromised computers (botnets) at the same time.
Though DoS/DDoS does not provide any direct benefit to the attacker in terms of ransom or phishing attacks, the mere satisfaction of denying legitimate requests is enough for some attackers to mount these attacks. Performing a DoS attack on a corporate resource is way more beneficial, having a direct impact on customer loyalty and brand trust. In some cases, attackers combine DDoS with other techniques to perpetrate a bigger attack, with DDoS being a precursor to taking the system offline from the network.
Types of DoS/DDoS Attacks
TCP SYN Flood Attack
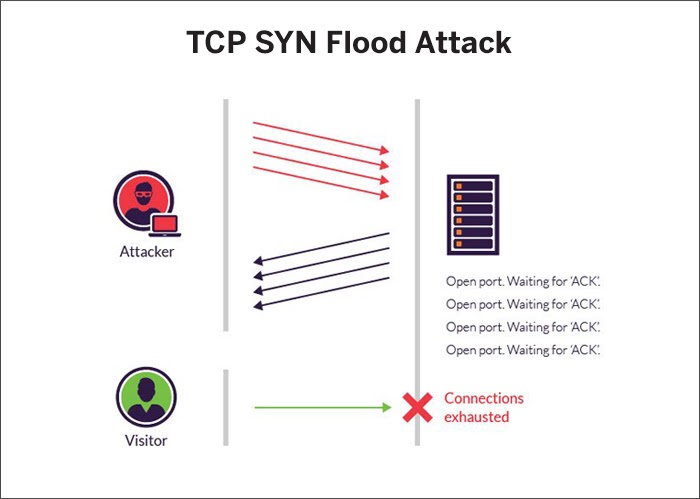
Source: Imperva
This involves flooding the system with multiple connection requests and exploits the buffer space during a transmission control protocol (TCP) session initialization handshake. The attacker’s system does not respond to the request from the target system purposefully and floods the system with requests. This makes the target system to time out and becomes unavailable for legitimate requests from other users.
Teardrop Attack
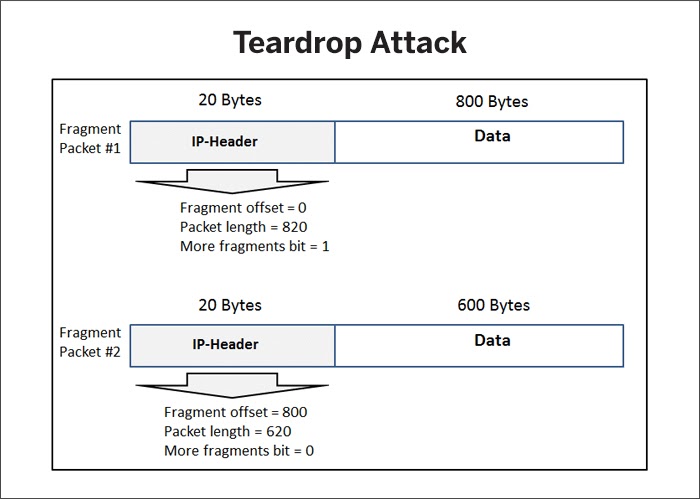
Source: ResearchGate
This involves sending fragmented information packets to a target system. The attack targets TCP/IP fragmentation reassembly bugs (found in older OS versions) and causes fragmented packets to overlap one another in the target system. Though the system tries to reconstruct the fragmented packets, it fails and crashes. Teardrop attacks typically use gigantic payloads.
User Datagram Protocol (UDP) Flood
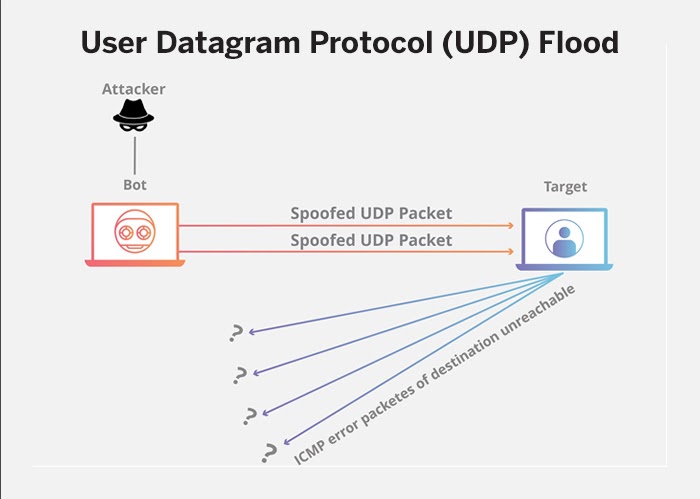
Source: Cloudflare
This involves flooding random ports on the target machine with packets, overwhelming its ability to process the UDP packets, and respond. In some cases, the firewall attached to the server becomes overloaded as a result of UDP flooding, causing the system to shut down.
Smurf Attack
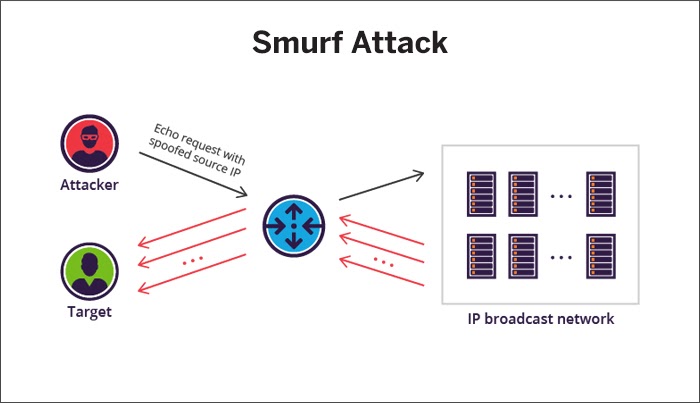
Source: Imperva
This involves IP spoofing (hiding the original IP) to saturate the target with overwhelming traffic and uses ICMP echo requests originating from a spoofed target IP. This request goes to all IP addresses in the specified range, with all the responses going back to the compromised device which overwhelms the network with time.
Ping of Death Attack
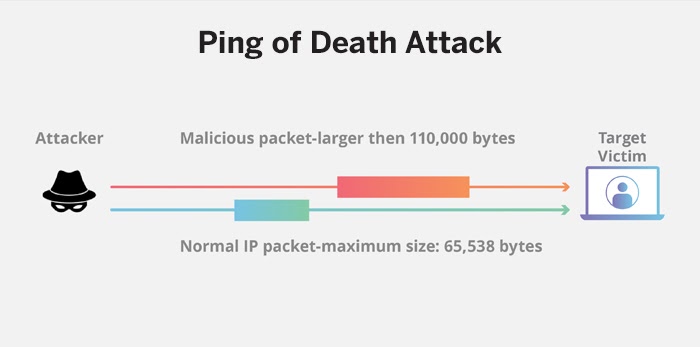
Source: Cloudflare
This involves sending IP packets with more than the allowed size of 65,535 bytes to ping the target system which does not have a patch to handle the attack. The attacker fragments the packets, which then reassembles at the target system. While doing so, the system may experience buffer overflows and crash.
Botnets
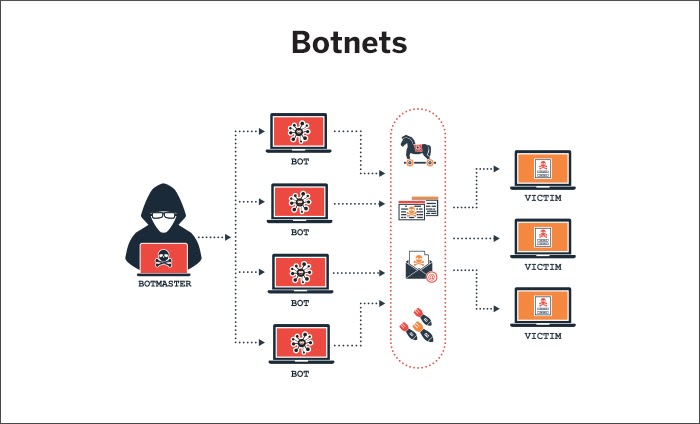
Here, multiple systems that are infected with malware from an attacker are used to carry out a DDoS attack. These zombie systems are on a mission to destabilize target systems by overwhelming their bandwidth and processing capabilities. Attacks through botnets originate from different geographical locations, and hence it becomes virtually impossible to trace the source of the attack.
Example of DDoS Attack
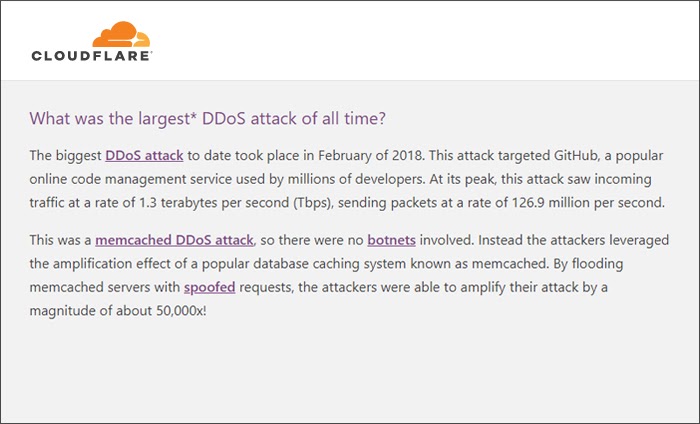
Source: Cloudflare
In February 2018, hackers targeted the popular code-hosting site GitHub in a massive DDoS attack. It is considered the biggest DDoS attack on a known victim. Though it lasted for a brief period, at its peak, the GitHub network received 1.3 terabytes of data per second at the packet exchange rate of 126.9 million per second. Since it was a memcached attack and not a botnet attack, attackers sent spoofed requests to memcached servers and ended up amplifying the intensity of the attack by a factor of 50,000. GitHub, is an advanced network involving thousands of coders all over the world, was able to detect the attack within 10 minutes and started the correction path immediately. The whole process lasted only 20 minutes, but the scale of the attack made it the worst mounted DDoS attack.
Guarding Against DoS/DDoS Attacks
Combating DDoS is quite difficult, as it is virtually impossible to trace the attacker and know the source of the attack. Since it is best to prevent a DoS/DDoS attack than being left scrambling after its occurrence, employing security and network perimeter tools to monitor the traffic usually helps in fighting DDoS attacks.
Monitoring for suspicious network activities should help. For example, unusual web traffic peaks should raise an alarm. Web administrators can employ ingress filtering methods, through which internet packets are correctly traced to their genuine IP addresses. Blocking spoofed IP addresses and stopping traffic coming from known malicious sources can help avert DDoS attacks.
It is a good practice to close unused server ports so that cyber-criminals do not exploit the vulnerability. Also, disabling IP-directed broadcasts at the routers level can help. Configure firewalls to handle SYN packets and monitor fragmented payloads for their max size to prevent PoD attacks.
Paid secured hosting solutions always help. Dedicated virtual private server hosting on cloud infrastructure, like AWS, can provide reliable and scalable hosting solutions, keeping DDoS attacks at bay. The use of proxy addresses can also come in handy to protect against DDoS attacks.
Cross-Site Scripting (XSS)
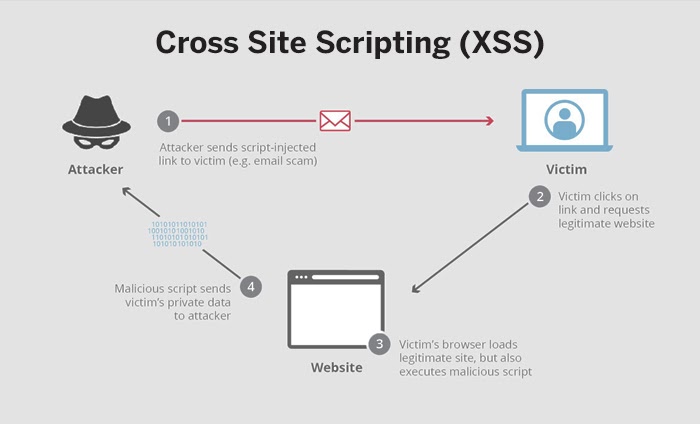
Source: Cloudflare
XSS features as a prominent threat in the OWASP Top 10 application security risks. They are a group of attacks where the attacker injects code or malicious scripts directly into a benign website without attacking the website itself. The attacker writes the script in JavaScript, Flash, Ajax, etc.
Whenever a user visits a compromised website, the client’s browser runs the script. Since the web browser does not recognize the malicious script, as it comes from a trusted source, it successfully runs as a browser-side script and captures cookies, session tokens, and other sensitive information retained by the browser. This not only damages the reputation of the website (as the attacker may even vandalize the website) but also hijacks any information that the user communicates with it, such as user credentials, credit card information, cookies, etc. What is worse is that neither the website administrator nor the user has any clue about the malicious code put in place, and may result in huge damages if not handled immediately.
Types of XSS Attacks
Reflected XSS or Non-Persistent XSS Attacks
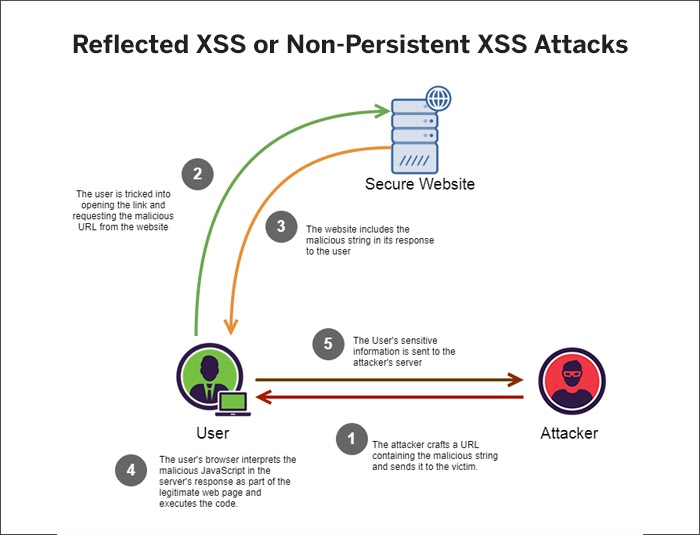
Source: Medium
These types of attacks happen when the application receives data in an HTTP request but includes the response in an unsafe way. The attacker passes the malicious script as a query in the URL and publishes it as a link or sends it in an email (phishing) to the user. When the user clicks on the link, the script executes. Since the query has unsanitized input values, the malicious script injects into the web page that the target system’s browser is loading and is executed by the browser. The attacker receives private data. In the case of sophisticated attacks, the attacker can perform any action in the application as a user and even initiate interactions with other users. Others would see the request coming from the compromised user, and thus get subsequently compromised as well.
Persistent XSS attacks (also known as Type 2 XSS)
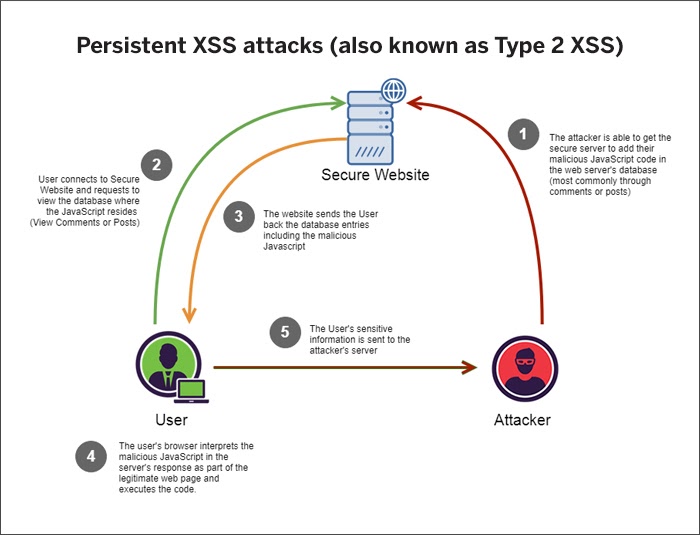
Source: Medium
These happen when the attacker stores the user input in the vulnerable server itself without performing proper validation. Unlike reflected XSS attacks, the user is compromised just by visiting the vulnerable web application. Other users visiting the compromised website receive the stored inputs and get the malicious script executed in their local browser, without performing any action. Though they are less prevalent, they are more devastating than their non-persistent counterpart.
DOM-based XSS Attack
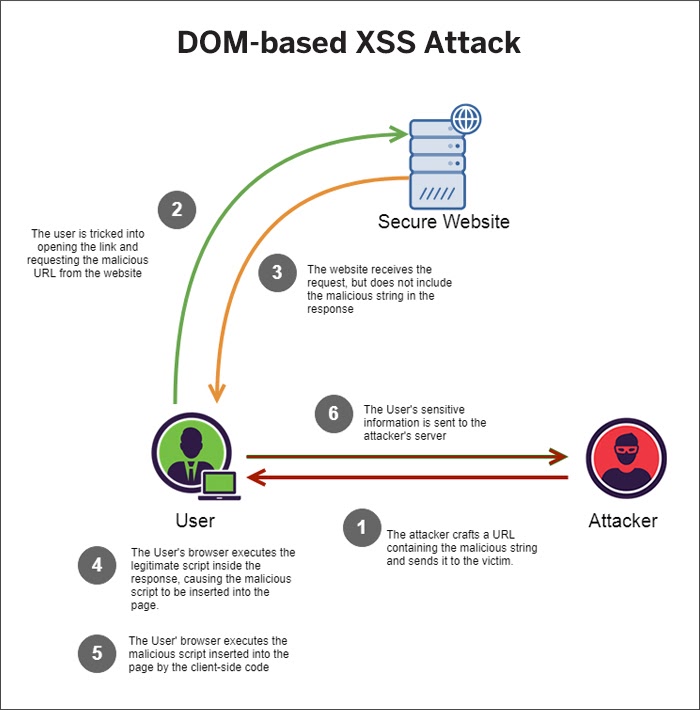
Source: Medium
This occurs if the web application writes data to the Document Object Model without proper sanitization. It occurs because of vulnerabilities in client-side scripts served by the application itself, rather than any payload provided by the attacker. The attacker can make use of DOM’s several objects to create XSS attacks. The vulnerable client-side script delivers the malicious script injected by the attacker to the target browser.
Example of XSS Attack
One of the most popular XSS attacks was carried through Samy worm, named after the American security researcher and hacker Samy Kamkar, who designed it to infect and propagate through MySpace. Though it did not cause much harm to the network, as that was not the intention of the hacker, it infected the social network quickly in a big way. The hacker launched it on October 4, 2005, and within 20 hours over one million MySpace user accounts had run it. As soon as a user ran this payload, their profile page would read “but most of all, samy is my hero” and send a friend request to Kamkar. MySpace soon fixed the vulnerability and reported Kamkar to the police.
Guarding Against XSS Attacks
Preventing XSS attacks listed above requires adequate security measures both at the client and server-side. With popular applications like Facebook and Google becoming prey to this attack, it becomes even more important to understand how to prevent XSS attacks and keep applications secure.
It is important to use secure coding practices, such as built-in sanitization, validation, and escaping functions. Escaping the user input data ensures sanitizing key characters in the user input before rendering it to the end-user. Escaping HTML and JS code and converting any special characters to their HTML/URL encoded equivalents helps in filtering out any opportunity to the attacker.
It is critical to manually test changes in the codebase and take the help of security testing tools to find reflected and stored XSS and redress the identified vulnerabilities before making the website live. Regular usage of a web application vulnerability scanning tool could help developers identify pain points in the application and redress them effectively to prevent any application security compromise.
Man-in-the-Middle (MiTM) Attack
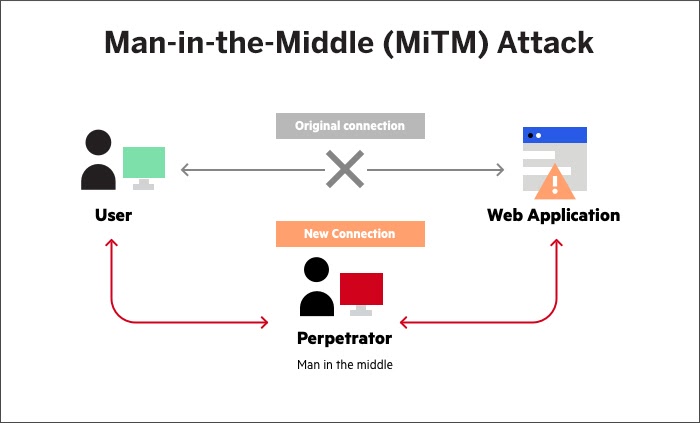
Source: Imperva
MiTM attacks happen when the hacker overhears the communication between the client and the server. The attacker overhears between two communicating systems illegitimately, hence the name. Each interaction between the client and the server gets a session ID, which is private to them. But, in the case of a MiTM attack, the intruder hijacks the session (through the XSS attack, for example) by capturing the session ID and poses as a legitimate resource and continuing the session with the server on behalf of the user. The invader gains access to unauthorized sets of information on the server and can wreak havoc. This attack comes in many flavors, like IP and DNS spoofing, replay attack, and session hijacking.
Types of MiTM Attacks
Rogue Access Point
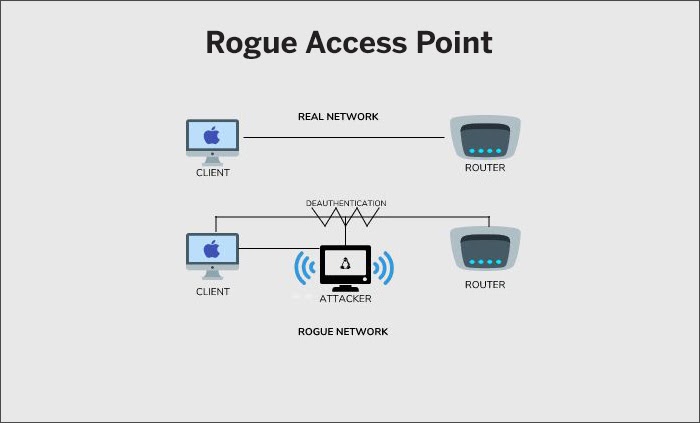
Source: Shellvoide
The rogue access point is an unauthorized node in the network but is still somehow operating. Using such open wireless access points, attackers may try to gain access to nearby devices. They usually come with no encryption or authentication, so that maximum devices in proximity can connect. The attacker, thus, compromises the network data.
Address Resolution Protocol (ARP)
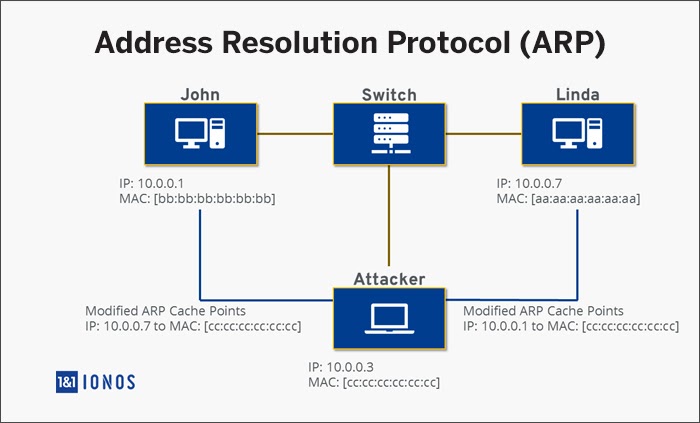
Source: Ionos
ARP resolves system IP addresses to physical media access protocol (MAC) addresses in LAN. Two hosts talk to each other by resolving IP addresses to the MAC address by referencing ARP. Using ARP spoofing, the attacker sends false/spoofed ARP messages. This causes their MAC address to map with the address of a legitimate computer in the network. This results in the attacker obtaining information intended for the original system, intercepting and modifying the data during transit.
Multicast DNS (mDNS) attack
Here, a DNS query is sent to all devices in the network in the same broadcast domain. The snooper carries out mDNS spoofing attack on LAN, just like ARP spoofing, with users not necessarily having to remember the addresses to which they connect. The attacker uses this protocol’s simplifying exercise to request with fake data and connects to the system as a trusted network. The victim’s system will show the attacker’s device as a trusted network, which can then control the device.
The attacker perpetrates MiTM attacks using several techniques. These include sniffing, where attackers employ packet capture tools and inspect network packets not intended for them. Additionally, the attacker uses packet injection to insert malicious packet data into the network stream, mixed with the legitimate data packets to evade recognition.
Session Hijacking
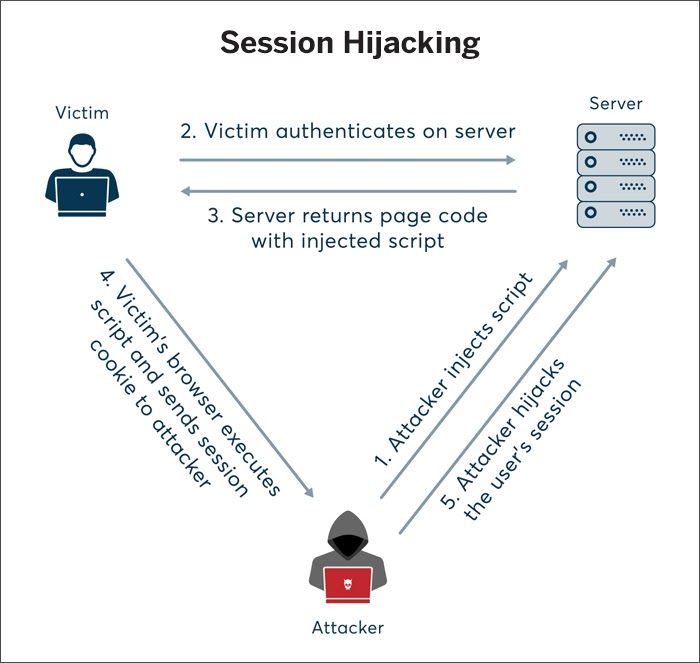
Source: Netsparker
Session hijacking is a prevalent MiTM attack vector. Through XSS, the attacker gains access to user session token and impersonates the user’s activities. After the hacker gets access to the session token, they have complete access to the user’s rights on the application.
SSL stripping, as the name suggests, involves stripping the secure layer from HTTPS to allow ARP or DNS spoofing. Attackers intercept packets to alter their secure HTTP requests to their non-secure HTTP equivalent, which passes on sensitive information as unencrypted, plain text information.
Example of MiTM Attack
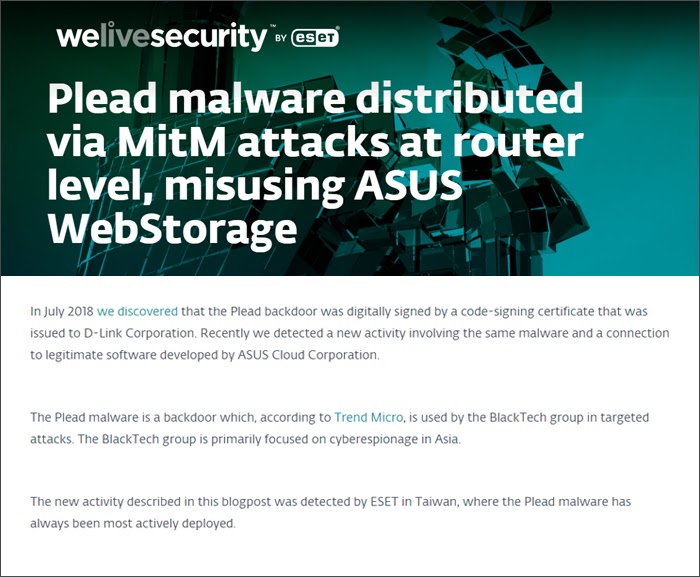
Source: WeLiveSecurity
In April 2019, the internet security company ESET discovered a MiTM attack by Plead malware in the ASUS network. The researchers noted that a Plead backdoor was created using a Windows-based process “AsusWSPanel.exe” for communicating with ASUS WebStorage. The researchers speculated that the malware was spread using MiTM attacks and compromised routers since the admin panels of routers are accessible through the internet, whose security can be easily breached. In such a scenario, the HTTP request sent by the ASUS WebStorage software carried a malicious link inserted by hackers, which forced users to download a file with a compromised PNG image. This Plead payload also included a Windows binary which persists at the start menu of the operating system. The ESET researchers concluded that companies needed to issue MiTM-resistant updates to protect client terminals.
Guarding Against MiTM Attacks
Preventing MiTM attacks is the best way forward rather than responding to them after they occur. Implementing strong Wi-Fi protected access (WAP) encryption on access points is a sure shot way to prevent MiTM attacks, as just about anybody cannot join a network and carry out a brute force attack.
Virtual private networks (VPNs) are a preferred way to exchange sensitive information on a network through encrypted communication. This makes it hard for attackers to decipher the network communication and masks the actual location of users.
The secure layer in HTTPS helps prevent intruders from tampering with the communication happening between the client and the server. Implementing only HTTPS connections without any HTTP alternatives for all network communications prevents packet sniffing to be of any use for the attacker.
Public key pair based authentication protocols, like RSA, can also help in securing communication happening between two hosts with defined public-private encryption and decryption processes.
Zero-Day Attack
The vulnerability may arise from a defect in your software, hosted application, or even hardware. It is usually a bug that escaped the attention of the testing team, and thus the development team does not know about it. In the case of known flaws, the development team does not have a patch in place to fix the flaw before releasing it to the production environment. This leaves vulnerabilities open for the attacker to exploit. Its name comes from the fact that there is a zero-day gap between the time of detecting vulnerability and a possible attack.
Open vulnerabilities in the web application leave the door ajar for attacks to take place before the technical team realizes a vulnerability’s existence. In many cases, the vulnerability may go undetected for months, with the developers coming to know of the bug only after a threat actor carries out an attack, and resultant symptoms show up as information loss of customers or credential theft. The developers then develop a patch for the vulnerability and avert further damage.
Example of Zero-Day Attack
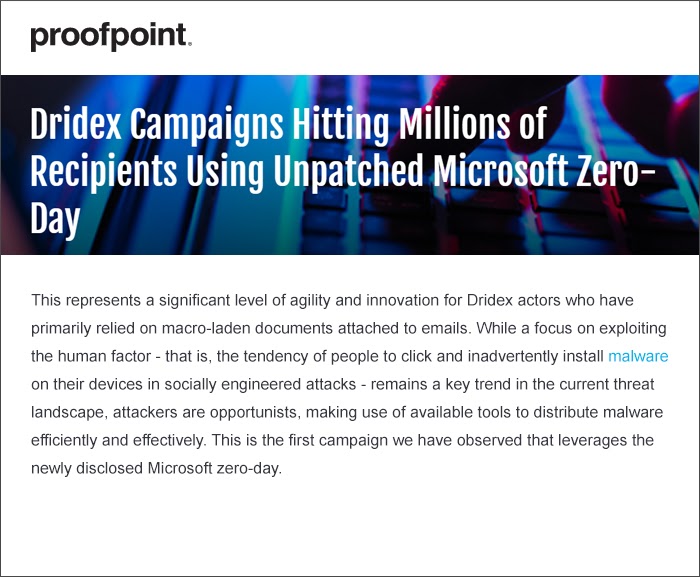
Source: Proofpoint
In early April 2017, a massive zero-day attack hit the users of Microsoft Word, primarily in Australia. It was part of a massive email campaign carrying the Trojan Dridex. When users downloaded and opened macro-laden Word documents from emails, they installed Dridex botnet and became victims of the banking Trojan. This malware was executed only when the infected Word file was opened with the “Enable Editing” feature on, which did not stop its spread since most users carelessly grant editing permission to downloaded documents. Microsoft realized the security lacuna soon enough and issued a patch on April 11, 2017.
Types of Zero-Day Attacks
The attacker goes through millions of lines of code, probing applications for their vulnerabilities using reverse engineering tools and techniques to reveal bugs or non-secure code. Once known, the attacker may use the information to propagate further attacks or sell sensitive information on the darknet.
Cyber-criminals used worms like Stuxnet to target computers in manufacturing industries in various countries, like Iran and Indonesia, by exploiting a zero-day vulnerability in Programmable Logic Controllers (PLC) which ran on Microsoft Windows. This shut down the centrifuges in Iran’s nuclear facilities, which is essential for the uranium-enrichment process.
Attackers could combine multiple attack vectors to exploit zero-day vulnerabilities in an application to create a long-lasting impact. Cyber-criminals employ techniques like spoofing, phishing, etc. to lure users in visiting websites with zero-day, and the hacker would benefit from the loophole to implant malware into the victim’s systems as they visit the website.
Guarding Against Zero-Day Attacks
It is important to detect zero-day vulnerabilities before they could be inappropriately used by attackers. Vulnerability scanning and security audits can help in the detection of zero-day exploits. The application can be made more robust and bug-free by simulating actual attack test case scenarios.
Peer code review against established benchmarks can help in finding previously unknown software vulnerabilities. This helps to sanitize the code quickly and update the application.
Rigorous testing for the detection of bugs/vulnerable code is a must for preventing run-ins with zero-day attacks. With the adoption of agile software development, iterations have become shorter and specific. Planned testing can help development teams to assure the quality of their products within the agreed client deadlines.
Instituting patch management as a defined practice to update codebase with patches regularly can reduce the risk of a zero-day attack. A seamless process to apply patches to redress bugs and quick application distribution post-patch is indispensable in maintaining a robust application, up-to-date with the latest patches.
How to Respond to Cyberattacks
Prevention is better than cure – this adage proves true for handling contemporary security threats. It is often less expensive to prevent a security event from happening than to do a postmortem analysis after the damage has been done. But, given a situation that a cyberattack has happened, we need to have in place a step-by-step protocol, including roles and responsibilities of personnel involved to assess the situation quickly and take immediate remedial measures to minimize the damage as far as possible.
A cyberattack warrant some or all of the following steps to take complete stock of the situation and remedial measures:
- Assess whether the security event is indeed real or just a scare. Some attacks may be minor and could be patched immediately, whereas others may be large enough to have multifarious impact on IT infrastructure of an organization. If the attack is real, then perform data backup immediately (if data is accessible and not compromised). Maintaining data redundancy (two sets of the same piece of data) can be of big help in such situations.
- Implement the cyber-incident plan, customized according to the type of attack.
- Inform the management and officials as part of the communication protocol. Present the facts as-is and inform them about the attack’s repercussions, activities planned to control the damage, and steps to prevent such attacks in the future.
- Notify legal authorities about the attack with possible digital footprint records of the attacker.
- In certain cases, insider attacks could be the source. In such a case, it is prudent to launch an investigation and take appropriate action on the perpetrator.
- In case of a DoS attack, activate the standby server to redirect the website traffic. Make efforts to re-launch the unserviceable server.
- In-house teams may fall short in handling big-scale cyberattacks. In such cases, do not hesitate to rope in cybersecurity professionals to assess and understand the damage and identify the vulnerabilities which caused the attack. Implement the suggested remedial measures which can prevent similar attacks in the future.
- Adopt utmost vigilance and monitor the web application firewall and other security systems in place aggressively for any untoward activity. It pays, in the long run, to invest in a comprehensive security solution, like AppSealing, to protect against wide-ranging, complex attack vectors.
Adopting the above steps can be a good starting point to reduce the impact of a cyberattack and pave the way to scrutinize, learn, and adopt security initiatives and best practices to prevent cyberattacks in the future.
Best Practices to Prevent Cyber Attacks
In the face of complex security threats and newly emerging attack techniques, howsoever robust a system/web application may be, it is never totally secure. This overarching reality, however, should not deter us from ingraining cybersecurity best practices, which act as the first line of defense in the event of a potent cyberattack.
Based on the observations made in the sections on different cyberattacks, let us have a look at the practices, techniques, and policies to prevent cyberattacks:
- Use a comprehensive anti-virus solution that tracks your employees’ online activities, websites they visit, and attachments they open, etc. to keep malware attacks at bay.
- Install a robust firewall and configure it appropriately to facilitate a secure online experience for your employees. A third-party firewall (in addition to the default internal firewall) gives the extra security cushion needed for your business. An email quarantine engine would help identify spam/phishing sources before delivering it to employees. You may also apply advanced security features such as runtime application self-protection to prevent attacks in real-time.
- Monitor your network regularly and investigate any suspicious activity immediately to prevent any untoward incident. Investing in comprehensive security suites, like AppSealing, can make all the difference between preventing a cyberattack and regretting the losses from a preventable cyberattack.
- Prepare a detailed cybersecurity policy document and adhere to it as far as possible.
- Train and educate your stakeholders, including employees and vendors, on how to conduct themselves safely while being online and make them aware of safe browsing practices and security policies.
- Schedule regular data backup (including cloud data) as an organizational practice and store the backup in a separate server. This habit prevents critical data loss in the event of a cyberattack, including ransomware attacks.
- Enforce strong and safe password practices to prevent security breaches, especially with multiple devices accessing data from company networks. Strong passwords are still one of the most elementary ways to enforce cybersecurity across the organization.
- Engage with security specialists and conduct a vulnerability assessment and penetration testing to identify loopholes in your application and undertake remedial measures to prevent your application from becoming a source of perpetrating malware/XSS attack.
In short, adopting a proactive approach is the only sustainable way to handle contemporary security threat scenarios. This approach should build a robust security architecture that addresses both network and application security needs of an organization.
Conclusion
Cyberattacks are here to stay with an evolving threat landscape. Estimates point that the complexity, audacity, and damage-afflicting ability of cyberattacks is set to rise with more people moving online to access digital applications in multiple ways. It is thus imperative for businesses to invest in solutions like AppSealing to adopt a proactive approach to deal with security threats effectively. This will go a long way to protect your brand image, ensure customer loyalty, and maintain data integrity, especially when your competitors may be reeling with security issues. Understanding cyberattacks is the first definitive step forward, which lets you adopt security measures to beat cyberattacks and stay ahead of the curve.
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.