An emerging challenge for bank applications, ensuring the security of banking applications requires advanced software security solutions coupled with forensic investigation methodologies and multiple layers of testing. Proof of the issue can be found in The “2023 Mobile App Security Threat Report” by McAfee which reported a 30% increase in mobile banking malware, indicating the time for a bulletproof approach to mobile finance applications that takes place over a much deeper level.
App Security in Banking Apps
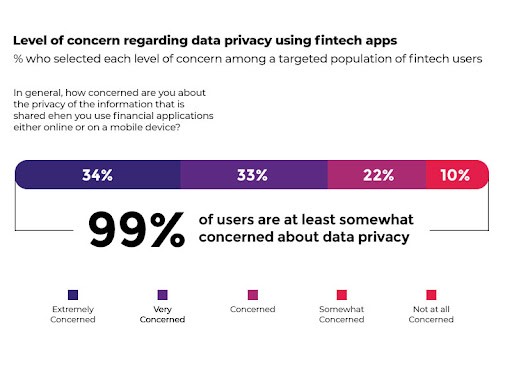
The surge in mobile banking attacks marks an unprecedented rise in cyber threats, with a notable 80% increase in banking Trojan incidents in the first half of 2021, as reported by a 2021 Threat Intelligence study monitoring over 200 million devices. These Trojans aim to capture SMS one-time passwords, significantly jeopardizing user security. The FBI’s cybersecurity alert in June 2020, prompted by the COVID-19 pandemic’s acceleration of digital banking adoption and the reduction of in-person banking, predicted a rise in attacks on mobile banking users.
The Dangers of Banking Apps’ Threats
Fake apps mimicking Barclays, Binance and Robinhood, among others, have been looting victims’ money by sending it directly to attackers. The “Super Signature” bypass just makes it that much more vital for financial entities to have strong anti-tampering and mobile piracy prevention because if they don’t, they could easily be exposing their users to extra jeopardy just to either cut corners or move faster.
Then overlay attacks such as the Xenomorph malware become that much more of a real threat. This type of malware tricks users into giving up vital data through interfaces that look like the genuine article. Not only is detecting these attacks important, but it’s also time to educate the public about what software like keyloggers (that’s the primary purpose of most of the software that’s implicated) really is.
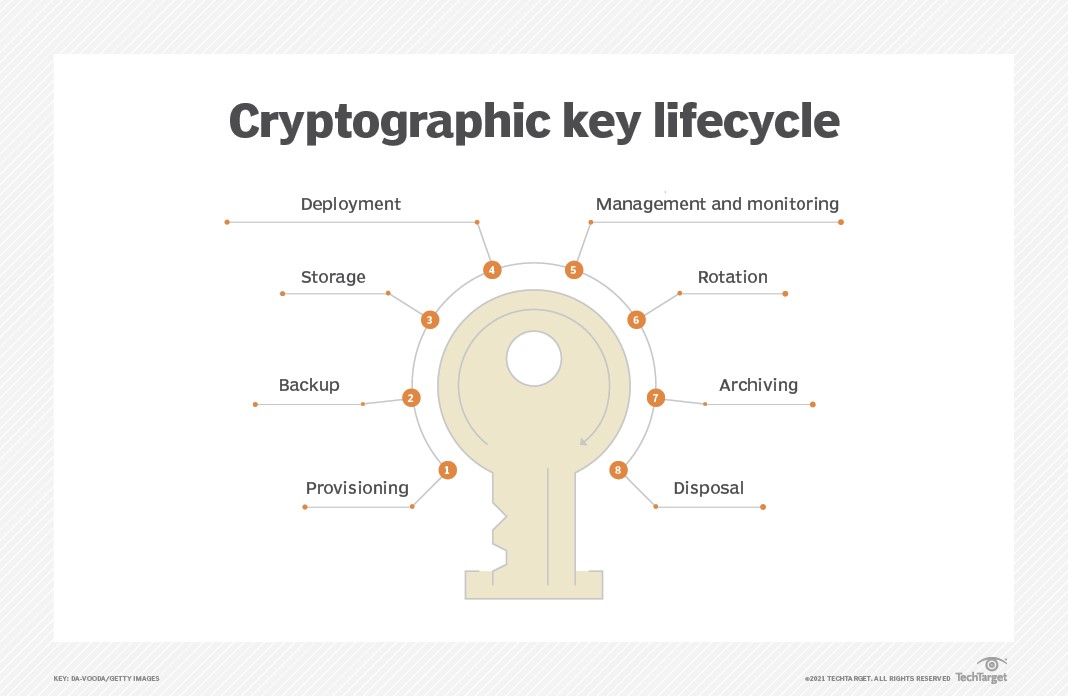
Protecting cryptographic keys is especially important in an era of digital finances. The shift from custodial wallets (where the wallet developer can always maintain the keys themselves) to non-custodial wallets (where you maintain your own keys, thank-you-very-much) are leaving wallet and app developers who have frequently never seen any of the security-related code they inherited in a world of hurt.
They’re finding out too late they wrote jailbreak/root/hack-emulated phone-running apps, didn’t encrypt their keys and stored data, and so many other such basic security sins that we are now all at the mercy of.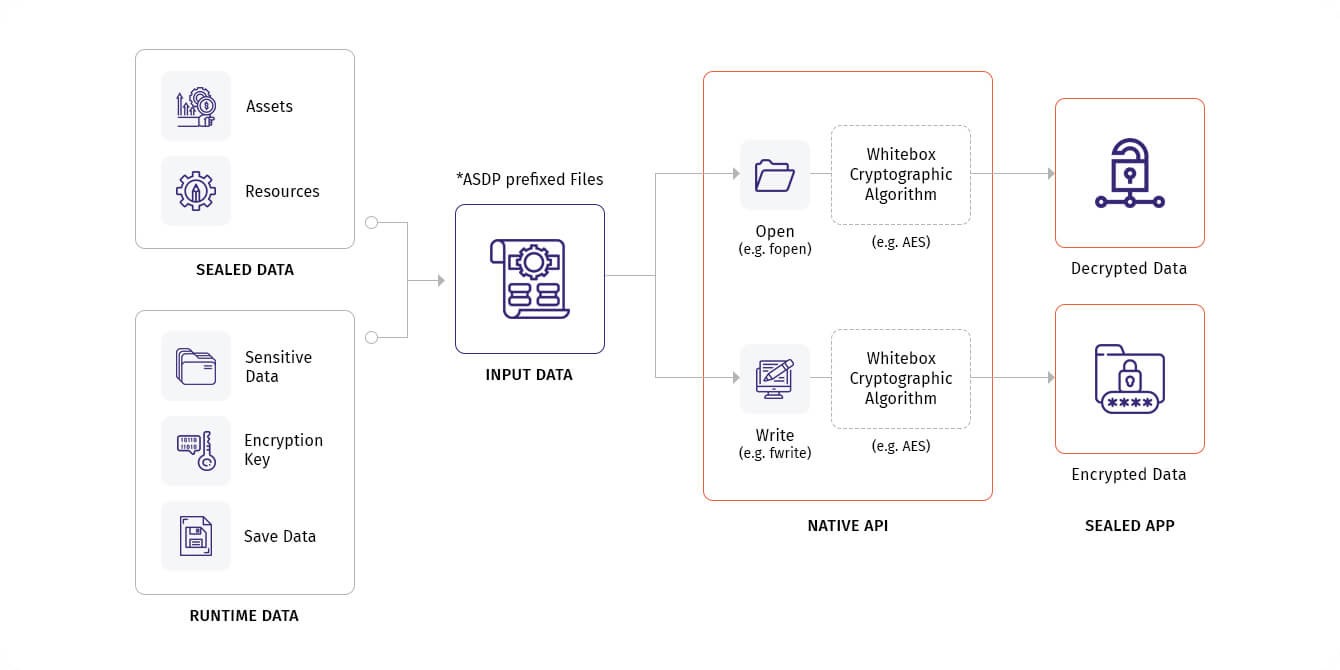
But we must secure the apps that are part of the present and near future of digital banking and fintech now. “Buy Now Pay Later” services are becoming so popular that you now have to have these usual (if it’s running on a jailbroken/rooted/.hacked emulated phone and other public data store) plus other safeguards in their app for synthetic identity fraud.
You don’t want to make it so easy to join your service that people can use the easiest scripted or human emulated channel to steal your profits, do you?
How AppSealing Mitigates Banking Apps Threats?
Screen Mirroring & Capture
From version 2.29.0.0 onwards, AppSealing has consolidated screen mirroring and capture detection into a singular function. This upgraded feature ensures that any attempt to view or capture the app’s screen using a screen capture tool will result in a black screen being displayed, thereby maintaining the integrity of the app’s content without forcing the app to close. Developers have the option to enable or disable this security feature using the “block_screen_capture” setting available in the Command Line Interface (CLI) tool.
Dex Encryption
DEX (Dalvik Executable) and ODEX (Optimized Dalvik Executable) files play a crucial role in the Android ecosystem, serving as the foundation for application initialization and execution. These files, which reside within an app’s APK, may multiply, leading to a scenario known as Multi DEX where an APK contains several DEX files.
To combat this vulnerability, AppSealing introduces DEX encryption, encompassing ODEX and Multi DEX files as well. This strategy implements an additional security layer, safeguarding the application’s code and assets against unauthorized access and theft. By doing so, AppSealing ensures that critical components of an app are protected, maintaining its confidentiality and resilience against hacking attempts.
QueryAll Packages
The “QUERY_ALL_PACKAGES” permission is pivotal for apps targeting Android 11 and higher with a targetSdkVersion of 30 or above, enabling them to access a comprehensive list of apps installed on a device. This capability is crucial for applications that need to survey the installed app ecosystem for various operational reasons.
In its version 2.28.1.0, AppSealing introduced a feature that allows developers to opt-out of using the “QUERY_ALL_PACKAGES” permission. Opting out means AppSealing will no longer perform a broad query of all installed applications.
Instead, it will specifically target a predefined list of known cheat tools by incorporating them into the <queries> section of the AndroidManifest.xml file.
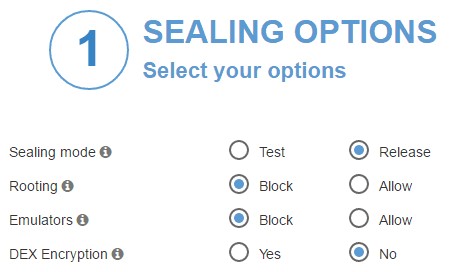
As such, it’s recommended to enable the “Block Rooting” feature to mitigate risks associated with sophisticated hacking tools like Game Guardian and Lucky Patcher, especially since the custom blacklist functionality becomes unavailable on devices running Android 11 or higher once this permission is disabled.
Wifi Security
AppSealing introduces a powerful Wi-Fi security solution that swiftly detects unsecured networks, alerting users immediately. This feature enhances users’ awareness of potential network risks, allowing them to make well-informed choices about connecting to unsecured Wi-Fi networks. By providing timely notifications about network security levels, AppSealing significantly improves both the safety of users and the integrity of network connections.
Fortifying Retail Apps Against Cyber Threats
Sensitive customer information, including identities, addresses, payment data, and purchasing behavior, lies at the heart of retail mobile application operations. A lapse in securing this information can lead to unauthorized access and compromise, possibly leading to identity theft, financial fraud, or diminished trust among consumers. Notably, the well-known women’s fashion retailer, Shein, faced a $1.9 million fine for not properly handling a data breach incident.
How AppSealing Mitigates Retail Mobile Apps?
Rooting:
AppSealing delivers thorough and uninterrupted safeguarding for mobile apps, preserving their integrity across both rooted and non-rooted devices alike. This sophisticated security approach provides applications with equivalent levels of safety as experienced on unrooted devices, through vigilant surveillance against unauthorized intrusions into the app’s memory, file system, firmware, among others.
Acting as a formidable layer of defense, AppSealing extends its protective services in a Security as a Service (SaaS) model, ensuring comprehensive security coverage for mobile applications.
Appsealing Android Emulator Detection
AppSealing’s Android Emulator Detection feature is equipped with two configurations: Block and Allow.
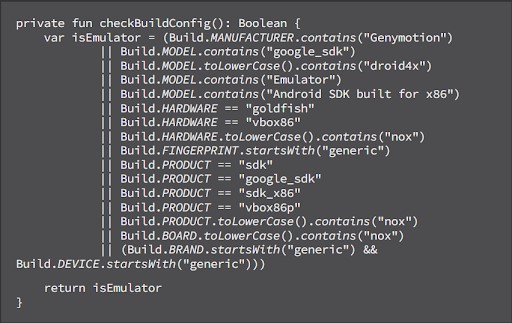
Block: This option proactively detects when the app is running in an emulator environment and subsequently shuts down the app. Given that most emulators possess features such as rooting capabilities, macro functionalities, and are operated on PCs, they pose a security risk. Activating the ‘Block’ function significantly lowers the risk of hacking, thereby bolstering the app’s security.
Allow: This setting permits the app to operate within an emulator setting. While this increases the app’s usability on various platforms, it simultaneously elevates the risk of cyber attacks. The inherent functionalities of emulators, such as rooting and macros, expose the app to potential security threats and hacking attempts, making it more susceptible to breaches.
USB Debugging:
AppSealing can block USB debugging The “block_usb_debugging“ (yes/no) option is available in the CLI tool.
Macro Bot:
AppSealing’s Macro Bot feature includes two key settings: Allow and Block.
Block (Default): This setting triggers the app to automatically close if any macro tool is identified on the device, serving as a default recommendation for enhancing app security by preventing the risks posed by macro automation.
Allow: With this option, the app remains operational on devices equipped with macro tools, offering operational flexibility at the expense of increased exposure to potential automated threats and exploits facilitated by such tools.
The Dangers of Fintech Apps Lacking Strong Security Measures
Our review indicates that a significant portion of these applications, ranging from unauthorized shopping APKs to complete breaches of mobile apps, shows a high susceptibility to security vulnerabilities, potentially deteriorating the consumer experience.
Vulnerabilities in Data Storage and Transmission:
Data that is not adequately protected within shopping apps or during its transmission across networks becomes a prime target for cyber interception and unauthorized access. Employing stringent encryption protocols to shield user data is crucial, ensuring its security both when stored on devices and transmitted over the internet.
Weak Authentication Methods:
Simplistic password and account verification methods facilitate the breaching of user accounts, highlighting the importance of implementing robust multifactor authentication systems to block unauthorized access attempts.
Exposure through Third-Party Services: E-commerce apps frequently rely on third-party services for payment processing or data analysis. Nonetheless, flaws in these external solutions can reveal sensitive user data and compromise the app’s integrity.
API Security Flaws: APIs are integral to the ecosystem of retail apps, enabling data flow between the app, backend servers, and external services. Inadequately secured APIs offer hackers a pathway to initiate data breaches or unauthorizedly alter app functionalities, potentially accessing sensitive information or critical app features.
Session Hijacking Risks: Cybercriminals can hijack user sessions, unlawfully accessing accounts and financial transactions if session token security or data transmission lacks proper encryption.
Man-in-the-Middle (MITM) Attacks: In MITM scenarios, attackers can intercept and possibly modify the communication between a user’s device and the e-commerce app’s server, risking the exposure of vital personal and payment information and subjecting users to significant privacy and financial hazards.
How AppSealing helps Provide App Security for Fintech Applications?
By leveraging AppSealing’s RASP capabilities, developers can focus more on creating and refining their app’s core functionalities while entrusting the platform to fortify their application’s security posture, thus achieving a quicker path to market with enhanced security measures.
Comprehensive Security Assurance:
AppSealing provides a robust security framework that automatically shields apps against a wide spectrum of threats. This dual focus on known and potential future vulnerabilities ensures apps are safeguarded throughout their lifecycle.
Zero Coding Security Integration:
The RASP feature by AppSealing delivers powerful security measures directly integrated into the app’s runtime environment. This is achieved without requiring developers to write a single line of code, simplifying the security implementation process.
Real-Time Threat Monitoring and Analytics:
AppSealing’s solution includes immediate detection and notification of security threats, backed by detailed statistical analysis. This enables developers and security teams to understand the nature of threats in real-time.
Efficient Threat Response:
Beyond just detection, AppSealing ensures a swift and effective defense mechanism is in place to counteract any identified threats, safeguarding the application against potential breaches or attacks.
Securing the Gaming Experience Through Robust App Protections
Given that a common denominator for gaming apps is the presence of vulnerabilities that may be ignored during development. These vulnerabilities present potential revenue losses when hackers exploit any overlooked weaknesses. The most common security threat landscape for gaming apps for which adequate security is not available can include:
Cheating –
Players may look to modify game files or leverage third-party tools to gain an unfair advantage.
Reverse Engineering –
Game manipulation can be another inciting factor for cyber adversaries. When hackers reverse engineer a game, they try to understand its coding to find vulnerabilities to exploit or create pirated versions of the game.
In-App Purchase Fraud –
Fraudulent transactions can not only result in revenue losses but it also hampers the gaming experience and the game’s economy.
Ads Patching –
Ad modification might not be inherently malicious, but still are damaging to a game developer’s revenue stream and involve:
Complete Ad Removal –
In this type of scenario, an ad version of your game could be decompiled, all ads removed and then redistributed on unofficial app platforms. The end result is that a new population of users who wish to experience a game without any ads discover the game through its illicit version.
Ad Reduction and Profit Redirection –
Rather than just eliminating ads, there are modified app versions in which fewer ads are exhibited while any ad revenue is redirected from the original developers to the modified app’s creators, meaning that the attackers are then profiting from the developer’s intellectual property.
Gaming Bots –
Bots are now the tool of choice for users who want to bypass engagement in the less exciting aspects of a game, automatically collect resources, and quickly build up their characters. These commercial games can not only have negative effects on a game’s economy, they raise additional concerns about the respective game’s integrity and security. This could undermine the authentic gaming experience and fair play for genuine users in genuine groups.
How AppSealing protects Gaming Apps?
With AppSealing’s advanced security features, gaming app developers can ensure their applications are protected from cyber threats, allowing them to deliver safe and engaging gaming experiences to their users.
Comprehensive Protection Against Threats:
AppSealing offers a robust security framework designed to safeguard gaming applications from a wide array of cyber threats, ensuring developers can focus on enhancing game features without compromising on security.
Seamless RASP Integration
The platform’s RASP technology seamlessly integrates into the app, offering a layer of protection that operates without the need for any supplemental coding from the development team, simplifying the security process.
Real-Time Threat Monitoring and Analysis:
With AppSealing, any potential security threats are immediately identified and analyzed, providing valuable statistical data that helps in understanding and mitigating risks promptly.
Efficient Threat Mitigation:
Beyond mere detection, AppSealing ensures rapid and effective countermeasures are deployed to protect the gaming application against any identified threats, safeguarding the app from potential vulnerabilities and attacks.
Cyber Security Landscape for OTT Apps
The security landscape for OTT platforms is fraught with challenges that require robust and adaptive security measures to protect both content integrity and user privacy.
Potential Risks for OTT Apps with Insufficient Security Measures
Challenges Posed by Inadequate Security in OTT Platforms
Content Piracy Resurgence
Content piracy employs sophisticated methods such as screen and audio recording to illegally distribute content. Despite industry efforts to standardize and secure digital content, the diverse range of devices makes it difficult to uniformly combat piracy.
DDoS Attacks on Servers
Attackers orchestrate Distributed Denial of Service (DDoS) attacks by overwhelming the server resources of an OTT platform with a flood of internet traffic from multiple sources. This can cripple the service, causing significant downtime and financial losses by rendering the platform inaccessible to users.
Reverse Engineering Threats
Hackers may decompile the code of an OTT app to analyze and modify it, embedding malware or creating a counterfeit version that provides free access to paid content. These tampered versions can then be distributed, endangering users by potentially harvesting their sensitive data.
Unauthorized VPN Use for Content Access
Users may exploit VPN services to circumvent geographic content restrictions imposed by OTT platforms, accessing content not available in their region. This not only violates content distribution agreements but also impacts the platform’s ability to enforce regional licensing laws.
Risk of Personal Data Leaks
OTT services that collect extensive personal identifiable information (PII) from their users are particularly vulnerable to breaches. Techniques like SQL injection and DNS spoofing attacks can exploit security weaknesses, leading to the unauthorized access and proliferation of user data.
How AppSealing and PallyCon Provides a 360 degree App Security for OTT Applications?
AppSealing introduces PallyCon offering a comprehensive cloud-based Multi-DRM (Digital Rights Management) license service coupled with Forensic Watermarking, PallyCon stands out as a complete solution for OTT platform owners seeking robust content security.
Forensic Watermarking:
A non-intrusive way to embed information within the content to trace the source of unauthorized distribution.

Visible Watermarking:
Adds visible identifiers to the content, deterring unauthorized sharing by making the source of the content easily identifiable.
Anti-Piracy and Monitoring Service:
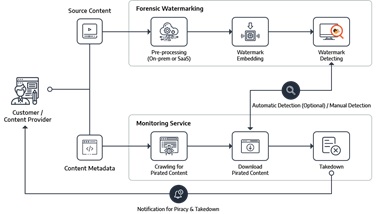
Proactively monitors the web for unauthorized distribution and use of the content, enabling swift action against piracy.
Anti-Capture Products:
Prevents the recording or capturing of content through various means, further securing content against piracy.
Comprehensive in-app RASP based security by AppSealing
The platform’s RASP technology effortlessly integrates into the app, providing a protective layer that functions seamlessly without requiring additional coding from the development team, streamlining the security procedure.
Conclusion
In the evolving landscape of digital security, the importance of robust protective measures across various sectors cannot be overstated. AppSealing, with its comprehensive suite of security solutions, plays a pivotal role in fortifying mobile applications against an array of cyber threats.
From banking and fintech to retail, gaming, and OTT streaming services, AppSealing offers targeted defenses designed to address the unique vulnerabilities of each sector. Its Runtime Application Self-Protection (RASP) technology, DEX encryption, and innovative features like anti-screen mirroring and capture, unsecured Wi-Fi alerts, and the proactive management of permissions through Query All Packages, set a new standard in mobile app security.
By integrating AppSealing’s solutions, developers can not only expedite their time-to-market but also ensure a secure, seamless user experience. In an era where digital threats are becoming more sophisticated, the contextual application of AppSealing’s security measures offers a beacon of hope, empowering industries to safeguard their digital assets and user data effectively. As we navigate the complexities of cybersecurity, the strategic implementation of AppSealing’s technologies emerges as an essential cornerstone for building trust and resilience in the digital world.