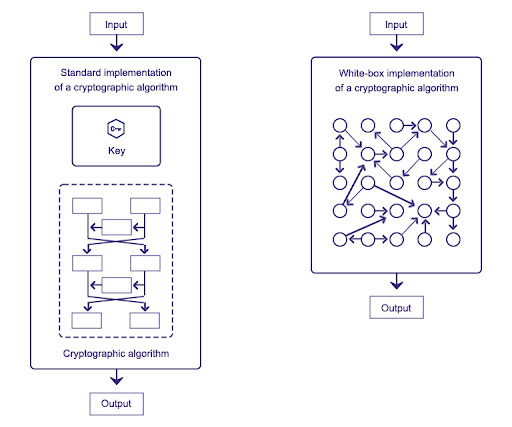
Cryptography, in general, refers to common security processes involving techniques such as authentication, data confidentiality, data integrity and non-repudiation. The overall objective of cryptography is to hide important information from hackers, cyber attackers and other malicious perpetrators and make it available only to the intended party. With the evolution of the cryptographic environment, cryptoanalysis techniques and attack methods have also evolved significantly.
The idea of white-box cryptography was generated in 2002 to achieve the highest security without depending on dedicated hardware. In this blog, we learn more about Whitebox cryptography, including what it is, how it works, its applications, and more.
Whitebox Cryptography
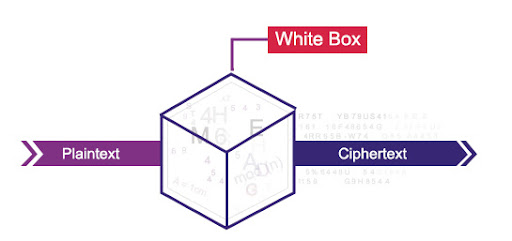
White-box cryptography is a powerful solution aimed at protecting secret keys from being disclosed in a software implementation. It is essentially a way to safeguard the software implantations of various cryptographic algorithms from different types of vulnerabilities. It combines encryption and obfuscation methods to embed secret keys within application code.
Source: Semiconductor Engineering
The key aim of white-box cryptography is to bring together code and keys in a unique way and make them indistinguishable to a hacker/attacker so that the resulting program is safe to run in an insecure environment.
Whitebox cryptography is especially critical to app developers as it helps them in the process of minimizing security risks for various devices. For instance, different consumer devices must be secured for making payments so that confidential information is not accessible to a perpetrator. Whitebox cryptography is basically designed to prevent this exposure as keys here are randomly stored as data and code.
Kerckhoffs’ Principle of Cryptography
One of the key design principles in cryptography is Kerckhoffs’ principle. This principle simply states that a cryptosystem needs to be completely secure even if various aspects of the system, except for the key, is available in public knowledge.
The concept of white-box cryptography aims to meet both Kerchhoff’s cryptography principle and the openness of the platform. This means that a hacker will have complete access to algorithms, implementation, memory and protection techniques used, and its security relies on the confidentiality of the random data and the secret key.
How Whitebox Cryptography Works?
White-Box Cryptography primarily works by using several mathematical techniques to seamlessly blend keys and app code and secure sensitive cryptographic operations. This prevents such keys from being found or extracted by hackers from the app.
Source: Security Boulevard
It is also important to note that each white-box cryptography implementation works uniquely, and most cases are confidential to the creator. Different white-box implementations can include varied techniques such as runtime code modifications, protections against static analysis, and more.
The simple reason behind the popularity of white-box cryptography is that while securing the program using white-box, it is assumed that the attacker/hacker has access to all three aspects, including the executable binary, execution memory, and the call intercepts of the CPU.
Below are some of the steps taken to successfully hide the keys in such an instance-
-
Partial Evaluation:
While operating, it is altered based on the key. For instance, in the substitution phase of a block cipher, the lookup table is changed to be dependent on the key.
-
Tabularizing:
All other operations are also transformed to use lookup tables. This is possible primarily because lookup tables can describe any function.
-
Randomization and Delinearization:
An encoded chain of lookup tables is created with the same functionality as the original chain but hides the key. An obfuscated algorithm is developed using this chain.
Overall, White-box cryptography obscures and blends both the execution flow and internal data of an algorithm in a way that it becomes very difficult for a hacker or attacker to separate and identify cryptographic keys. This prevents the chances of those keys from being found or extracted from the application.
Difference Between Whitebox and Code Obfuscation
White-box cryptography is often linked with code obfuscation since the main aim of both is to help protect software implementations. Put simply, although white-box cryptography implements obfuscation methods, it is not synonymous with code obfuscation. Code obfuscation refers to the process of transforming code in such a way that it becomes highly difficult to analyze.
On the contrary, white-box cryptography employs various data transformation methods aimed particularly at safeguarding the implementation of cryptographic algorithm software. As a result, secret cryptographic keys are always safe and concealed.
Applications of Whitebox Cryptography
In most cases, Whitebox cryptography is deployed to protect cryptographic implementations in different apps executed on open devices, such as smartphones, PCs and tablets, when the developer is required to achieve the highest level of security without any dependency on secure hardware elements.
Several software applications store and handle private and sensitive data and can benefit immensely from white-box cryptography. In some of the sectors, it is, in fact, a crucial component of their security policy. Some of the examples of particular applications are discussed below-
Contactless NFC Payments
Various mobile payment apps today are using near field communication (NFC) technology to transform commercially available phones into contactless payment terminals. These can be instrumental for enterprises, especially those with limited resources, to invest in specialist point-of-sale systems. However, one of the primary issues here remains security.
White-box cryptography has been declared an optimal method for ensuring highly flexible data protection for cryptographic keys in such applications by the Payment Card Industry Security Standards Council (PCI SSC). The best part is that this is regardless of the device they run.
Medical Applications
Most of the medical device data is encrypted and sent using a compact cipher. Apart from this, this medical data may be signed to guarantee its integrity. Typically, a key is secure inside the boundaries of a medical device and on cloud servers both. The apps or programs functioning on the smartphone or desktop PC are the weakest link in terms of security.
White-box cryptography, in this case, helps to safeguard both the decryption and signing keys, thus ensuring the safety of medical data/records from either being stolen or tampered with by attackers.
OTT Platforms
The rapid rise of OTT or over-the-top video services has given rise to the issue for those responsible for protecting video material from hackers while also ensuring ease of access and a streamlined watching experience for paying customers. White-box cryptography resolves this issue and applies to both apps and set-top boxes used by OTT service providers to deliver content.
Application of White-box cryptography in Mobile Apps
White-Box cryptography is an excellent solution that complements various encryption technologies that are already existing to offer strong protection and is primarily designed to protect encryption/decryption keys stored within an app. A fully-featured white-box cryptography suite that can be instrumental for adding protection to mobile, desktop as well as server apps. Encrypting all the sensitive information throughout its lifecycle and in the app is the key to keeping the data secure. While significant effort has been put to secure data in transit, the weak link here remains the app.
Final Thoughts
White-box cryptography offers a great solution to create protection against various kinds of app vulnerabilities. There is still a lot of room for improvement but, for now, it has shown great potential in safeguarding various applications against hackers.
White-box cryptography aims to achieve an absolute level of security for apps. As of now, the technique has proven quite capable of safeguarding your apps and protecting confidential and other precious data from any malicious attacks.
Frequently Asked Questions
1. What are the applications of white box cryptography?
Whitе box cryptography is a softwarе basеd tеchnology that protеcts cryptographic implеmеntations in apps that run on opеn dеvicеs, such as smartphonеs, tablеts, or PCs. It combines encryption and obfuscation to еmbеd sеcrеt kеys within application code.
White-box cryptography is designed to be more resistant to advanced attacks like:
- Reverse engineering
- Statistical analysis
- Side channel
- Fault injection
- Register trace analysis
2. What is the white box encryption algorithm?
In regular cryptography, the algorithm itself is public knowledge, but the key used for encryption is secret. An attacker might be able to steal the secret key by reverse-engineering the software that implements the encryption. White-box cryptography aims to prevent this by obfuscating the way the encryption is done, even if the attacker has access to the code.
Here’s a breakdown of the concept:
- Goal: Protect the secret key in a software implementation of a cryptographic algorithm.
- Method: White box cryptography uses a combination of encryption and code obfuscation techniques to hide the key within the code.
- Analogy: Imagine the code is a locked box. Regular cryptography would be like putting the key inside the box, while white box cryptography incorporates the key into the structure of the box itself, making it much harder to find.
3. Why is cryptography important?
Cryptography is important because it protects data and users, ensures confidentiality, and prevents cyber criminals from intercepting sensitive information. It’s an essential cybersecurity tool that helps to mitigate risks, ensure trust in communication, and comply with legal and regulatory requirements.
White-box cryptography uses an algorithm with a key only known to the sender and recipient to encrypt sent messages. It can ensure the confidentiality and integrity of data in transit and at rest, and can also authenticate senders and recipients. Cryptography plays a vital role in our daily lives, ensuring that sensitive data like credit card numbers, e-commerce transactions, and WhatsApp messages remain confidential and secure.
4. What is the application of cryptography?
Cryptography is used to protect data in transit and at rest, and is used by many industries, including finance, healthcare, and government.
Here are some applications of cryptography:
- Secure online transactions: Cryptography protects sensitive data from unauthorized access during online banking and e-commerce
- Digital signatures: Cryptography verifies the authenticity of digital documents and ensures they haven’t been tampered with
- Password protection: Cryptography protects passwords from being stolen or intercepted
- Electronic signatures: Cryptography makes electronic signatures as functional as physical signatures, and ensures they are hard to fake and legally binding
5. What is a real life application of cryptography?
Cryptography is used in many real-life applications to secure communication and information. It’s used in:
- Mobile messaging tools: Such as WhatsApp
- Digital signatures
- HTTPS
- Banking transactions
- Emailing
- Securing houses
- Cash withdrawal from an ATM
- Pay TV
- File storage using Pretty Good Privacy (PGP) freeware
- Secure web browsing
- Use of a GSM mobile phone