A while ago in 2017, a vulnerability in the certificate pinning technology exposed some major banks’ customers to man-in-the-middle attacks. This flaw was found in apps of banks like HSBC, Santander, Allied Irish Bank and NatWest, owing to which attackers from the same network as the victims’ could easily perform man-in-the-middle (MiTM) attacks. Standard tests to detect possible attacks were failing. The banks then took specific measures to update their apps to make them more secure and protect against such attacks in the future. This was one major MiTM attack that shook the financial world.
What are Man-in-the-middle (MiTm) attacks?
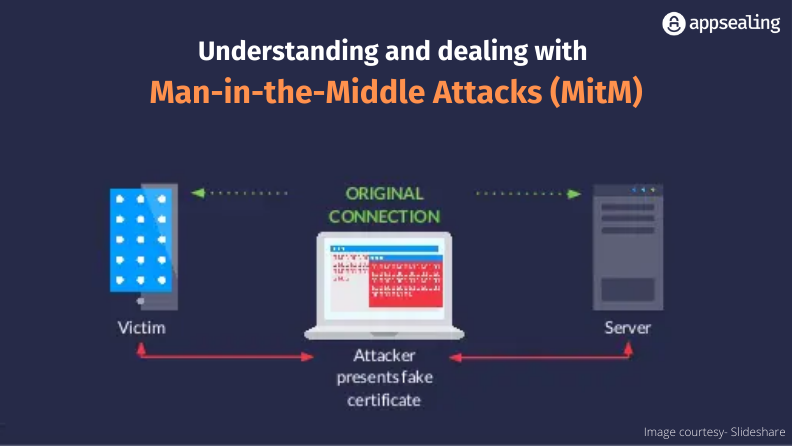
A man-in-the-middle (MiTM) attack is an attack where an attacker positions himself or herself between two users to overhear their conversation or interrupt a data transfer. A common type of cyberattack, an MiTM attack sees an attacker intercepting communication and message exchanges between two parties by literally inserting themselves as a silent observer and manipulator.
Every time a user interacts with a server/website, a session ID is created. The attacker, through an MiTM attack, secretly captures the session ID to eavesdrop and manipulate the content with the intention to ultimately steal data like login credentials, financial data or other personal information with the aim to misuse it for transactions, identify theft or password change. It could also be used for devising advanced-persistent threat (APT) assaults in the future. There are 3 players here – the victim, the person / application that the victim is interacting with and the attacker.
How do MITM Attacks Happen?
MITM attacks follow a straightforward approach wherein an attacker first obtains access to a conversation and starts eavesdropping. Then the attacker becomes the man in the middle to intercept any messages that are shared between two parties. Then, the attacker either steals the data or alters any messages to gain control over the conversation and perform financial transactions (if any). There are two types here:
Network Traffic Interception:
This type is observed when there is a “free wi-fi” available and someone connects to it. The wi-fi provider can then steal the data in the background.
Mobile App Network Security:
This type comes from the well-known debate between HTTPS and HTTP. While it is common sense to use HTTPS and most applications use the same, it would be surprising to know that many developers configure it incorrectly, leading to many security loopholes.
Mobile Apps and MITM Attacks
MITM attacks in mobile apps are a common occurrence owing to incorrect certificate validation, limited standard authentication methods (other than HTTPS) or unsecured protocols. Certificate pinning can help establish robust authentication by linking an app’s certificate to the destination’s hostname. These controls need to be built within the app itself. Such attacks can lead to illegitimate access to personal information, financial data, location, messages, conversations etc. Validation of hostname, insisting on HTTPs usage and certificate matching are some ways to ensure secure connections.
Types of MiTM Attacks
Multiple types of MiTM attacks are used to target victims. A couple of them are:
Email Hijacking:
Here an attacker targets the victim’s email address to gain access to the communication between a target institution (for example: a bank) and the victim. Special attention is given by the attacker to transactions that happen between the two parties. From here, the attacker can spoof one or both parties to send specific instructions. For example, the attacker can spoof a bank’s email id to request some sensitive information to hack into the victim’s account or perform fraudulent transactions.
Session Hijacking:
This occurs through a cross-site scripting (XSS) attack or by stealing session browser cookies. For example, when a user logs into their bank account, an attacker might be watching and stealing the session cookie while the session is still on. Now the attacker can go on to transfer all the money from that account to his own.
Wi-Fi Eavesdropping:
Here an attacker sets up legitimate-sounding Wi-Fi connection names or public Wi-Fi connections which do not require any password. Users are lured into connecting to the network thinking they could simply browse the network at no additional cost or effort. For example, a user might see a Wi-Fi network named ‘New York Airport’ making them think that it is a legitimate Wi-Fi connection provided by the New York Airport authorities. Once they connect to the malicious network, the attacker will be able to access the activities performed by the victim.
IP Spoofing:
The attacker alters packet headers in an IP address. For example, if a user is attempting to access a legitimate ecommerce site for example and the IP address header is manipulated, the user will now be redirected to a fake similar-looking one. When a transaction is initiated, the funds are transferred to some other accounts.
DNS Spoofing:
Also known as DNS cache poisoning, this process sees a hacker infiltrate a DNS server and alter the website address record to match their own record. For example, if a user is trying to access a legitimate website and DNS spoofing occurs, the user is redirected to the fake address through the altered DNS record. If now the victim sends any sensitive information, that will be routed to the attacker.
HTTPS Spoofing:
Here, domains that look exactly like the original HTTPS one with minor changes in non-ASCII characters are used to lure victims who think they are conversing with legitimate websites
SSL Hijacking:
Secure Sockets Layer establishes secure connection between two devices. Through SSL hijacking, the communication is encrypted and attackers can access all the information and misuse it.
Browser Cookie Theft:
Here, cookies are hijacked to gain access to users’ passwords, personal details, transaction details etc.
ARP Spoofing:
Address Resolution Protocol (ARP) helps translate a machine address (MAC) to a local IP address. In ARP spoofing, an attacker links his machine address to a legitimate user’s IP address through fake APR messages. Any data sent by the user is then transmitted to the attacker.
Rogue Access Point:
As the name suggests, here attackers set up their own rogue wireless access points with the understanding that many wireless cards try to automatically connect to nearby access points. It works on the principle of proximity.
mDNS Spoofing:
An offshoot of DNS spoofing, here an attacker uses a local area network (LAN) to respond to legitimate requests with fake data redirecting the user to an illegitimate site.
Detecting MiTM Attacks
Detecting these attacks can be difficult since a lot happens in the background. But fret not, as we list down a couple of incidents or activities to look out for which can help send red flags for sure:
- An unexplained delay in loading pages or applications
- URLs starting with ‘Http’ instead of ‘Https’
- Repeated disconnections and interruptions in the app
- Strange addresses or characters in the application URL
Preventing MiTM Attacks
As a company looking to secure your application data, you can incorporate the following best practices to prevent MiTM attacks:
Implement WAP Encryption on Access Points:
Strong wireless application protocol (WAP) encryption prevents attackers from hacking into systems
Usage of VPN:
A VPN for monitoring traffic between end points and the server can limit MiTM incidents. Since it uses key-based encryption, attackers from nearby shared networks will not be able to penetrate the system
Stick to HTTPS Connections Only:
This will prevent hackers from stealing information. Browser plugins are also available to enforce this rule and ensure HTTP counterparts are never used
Implement End-to-End Encryption for all Types of Communication:
Ensure to cover a whole range of communication systems like email, chat, website, video etc.
Educate Employees:
Empower your staff to look for regular signs and alert relevant teams in case of any incidents so it is never too late to take action
Invest in Strong Authentication Protocols:
A public key-based authentication or RSA can help strengthen passwords through asymmetric cryptographic algorithms having public and private keys. Whenever a user tries to log in to a system, the server would ask them to enter a public key (stored in the place that they want access to) for authentication purposes. This is followed by a private key (which is kept secure in the user’s computer)
Get Your Basics Right:
Keep your security patches updated, use a password manager if feasible, undertake regular monitoring procedures and invest in multi factor authentication
Invest in RASP:
The sheer number of incidents and the complexity of attack vectors put a special emphasis on application security in real time. Human intervention is just not enough to detect and prevent attacks. Especially in the case of an MiTM attack which is usually silent and happens in the background before the damage is done, runtime application self-protection (RASP) makes more sense. It helps enterprises scan their applications in real time to detect attacks and possible vulnerabilities. It proactively looks for attacks and even suggests measures to stop them. This is how it is better than web application firewalls.
It is important to test protection levels and protocols through some best practices like the following:
- Certificate testing: Through a proxy, app developers can test the certificate type apart from checking the security of endpoints
- Overcome false positives: Set up an interface to collect data using iptables rules and forward traffic to a proxy of your choice. This will ensure that apps can proxy off an interface instead of a device
- Cover jailbroken and rooted devices: When it comes to certificate pinning, use dynamic instrumentation tools to check for any bypassing of rules
Conclusion
Owing to so many devices being connected over the Internet and Cisco predicting that the number will touch 27Bn in 2021, MiTM attacks will also witness a major jump. A good starting point to deal with these attacks is to first detect them through some common tell-tale signs as highlighted above. Then, the damage control becomes easier. Agile, ever-growing organizations should look for longer term solutions like RASP to proactively scan for issues before they snowball into something far more serious. AppSealing’s complete in-app security solution can help you monitor such attacks in real time and stay away from them.